Protect your mission-critical applications and APIs from advanced cyber threats with powerful custom workflows
- Graphic workflow technology
- Enhance security
- Detecting malicious bots
- Avoid false positives
- Adapt to IP Reputation
- Customize dashboards
What is possible with UBIKA WAAP Gateway?
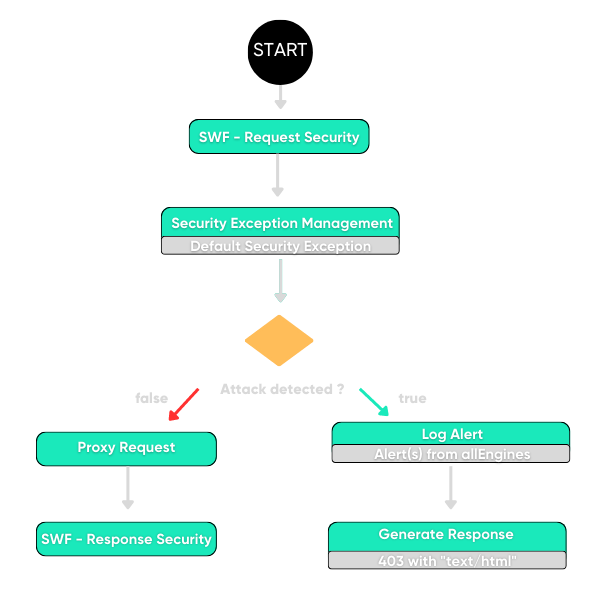
Develop security policies with our graphical workflow technology
UBIKA WAAP Gateway has a graphic intelligent management interface that allows you to visualize traffic processing and flow. Chain multiple security engines through the workflow for accurate detection and reduced false positive rate. Plus, you can switch from blocking to logging mode on all or part of the security policy with a single click.
Strengthen API security with additional engines
The solution allows validating JSON/XML structure using schemas and paths using OpenAPI validation. In addition, the optional Advanced Package feature enables additional engines in the workflow to enhance your API security and extend it to custom applications and machine-to-machine communication. The Advanced Package allows enterprises and public authorities to retain the agile advantage of API-based development while ensuring security and compliance.
Detect and mitigate malicious bots, to ensure legitimate traffic
Malicious human-like bots, which are difficult to detect, are the source of most attacks on the web. Bot mitigation is an intelligent feature that verifies the source of a traffic request (a human or a machine), then controls the request via a challenge-based protection technique.
Avoid false positives with automatic and advanced resolution
.
The more accurate a security model is in identifying an attack, the lower the number of false positives. Not only is the speed of exception creation important, so is its accuracy. The auto-resolve feature automatically creates accurate exceptions in security exception profiles and allows for the resolution of one to several hundred logs at once.
Adapt to IP Reputation, user behavior and context-specific scenarios.
The solution uses Webroot’s real-time threat intelligence database to protect customers from IP threats. It handles both blacklists (deny lists) and whitelists (permission lists). It can work with OpenAPI files and enforce them on traffic. In addition, it uses the scoring model to increment a score so that if the score is greater than the defined limit, the request is blocked and redirected.
Define and customize dashboards for advanced monitoring and reporting.
UBIKA WAAP Gateway monitors user activity in context to prevent attacks on application logic and blocks anomalous behavior. The reports combine executive, managerial and technical level views, support customizable templates and show the evolution (diff) over time. They are available in four different formats (PDF, XML, CSV and MHT) and in multiple languages.
UBIKA WAAP Gateway Advanced Package
Our bespoke security modules provide the highest level of protection for your business, ensuring peace of mind and confidence in your operations. Choose the UBIKA WAAP Gateway Advanced Package for complete, customised protection for your applications.
White list - Open API3
Are you concerned about the security of your APIs? Do you want to implement your API security policy easily? Do you want to protect your organisation against the most common API attacks?
- Improve the security of your APIs.
- Apply a security whitelist.
- Enable collaboration between your development teams.
- Easy, human-readable generation: OpenAPI 3 allows you to define your API endpoints, parameters and responses in a machine-readable format that is easily converted and human-readable
.
WebSockets flow security
Securing WebSockets is essential to protect against security threats such as cross-site scripting (XSS), injection attacks and data breaches.
- Secure WebSocket traffic.
- Block WebSockets messages completely.
API encryption
The API Encryption module strengthens the protection of the integrity of APIs owned and used by customers. This functionality is directly integrated into UBIKA WAAP Gateway using the same worflow configuration.
- Advanced filtering of XML and JSON APIs.
- Jeton Web JSON to integrate industry standards for authentication
API authentication standards (OAuth, OpenID Connect). - Validation of JSON / XML schemas (checking data content conformity).
- Obfuscation, filtering and manipulation of JSON / XML data.
- XML encryption, signing and XSLT.
-
20+
Years of experience
-
100%
Scalable and automated
-
600+
Customers trust our solutions
Used by 600 customers
We are recognised by our customers as a Strong Performer in 2022 for web application and API protection solutions.
The challenges of traditional web application firewalls (WAFs)
Reducing false positives
Most WAFs do not offer a simple way to manage false positives, resulting in high administrative costs.
Block 0-days
OWASP Top 10 list attacks, zero-day attacks, API security threats, etc. are still a major threat to web applications.
Fix vulnerabilities in production
It takes more than a month to fix a critical vulnerability. Updating an application to fix it can have side effects and affect the business.
What does set us apart?
Robust security
Use multiple security engines built on 20+ years of application security expertise.
Ease of use
Take advantage of our unique wokflow visualization that accommodates even specific out-of-the-box security scenarios.
YesWeHack Partnership
Discover new vulnerabilities on the YesWeHack platform and request a virtual patch with our solution – faster 360X resolution.
Find out about Additional Services.
Our team of experts offer customized support.
- Expertise
- On-demand services
- Managed Services
- Training and Certification