How do you protect against computer obfuscation with a WAF?
What is obfuscation?
Obfuscation in IT refers to all the methods aiming at altering the readability and the understanding of a part of a source code without changing its functioning.
Application protection through computer obfuscation…
Obfuscation can be used as a tool to protect an application in production in order to avoid its “reverse engineering”, i.e. the possibility for an external user to understand the source code in order, for example, to exploit potential vulnerabilities.
With this in mind, it is possible to replace variable names with characters such as the underscore “_” in order to give no information about their usefulness.
… but also a tool used by hackers
However these techniques can just as well be used for malicious purposes, regarding the security of web applications, obfuscation allows to bypass some restrictions, these can be security mechanisms directly in the source code or web application firewalls.
Obfuscation is therefore a double-edged tool, being as effective in protecting an application as it is in attacking some.
What is the difference between a normal attack and an obfuscated attack?
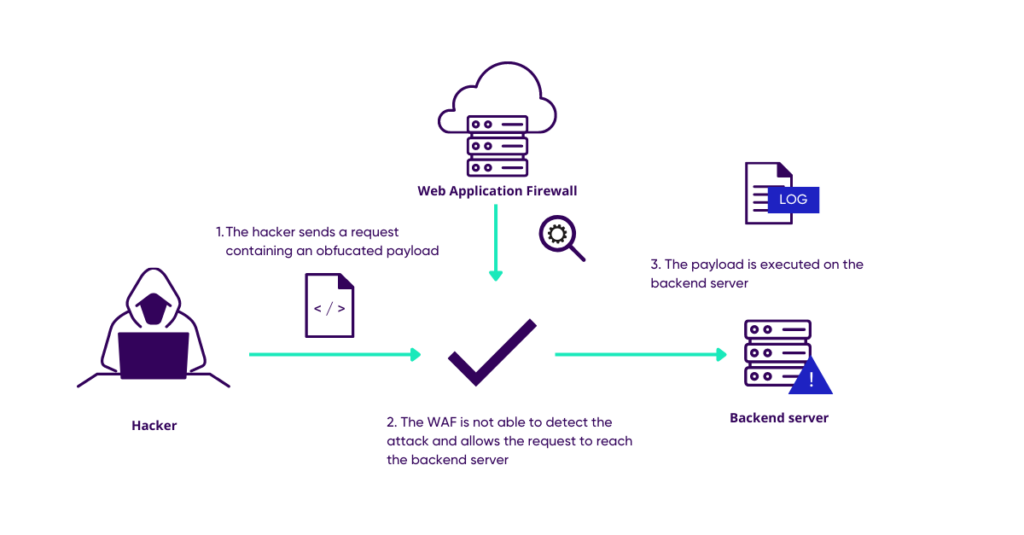
1. Normal attack scenario
In a normal attack, the attacker simply sends an attack aimed at a company’s server, such as a command injection, however the web application firewall will analyse the request and spot the attack.
As the request is not healthy, the user cannot access the server and their attack attempt is recorded in a log.
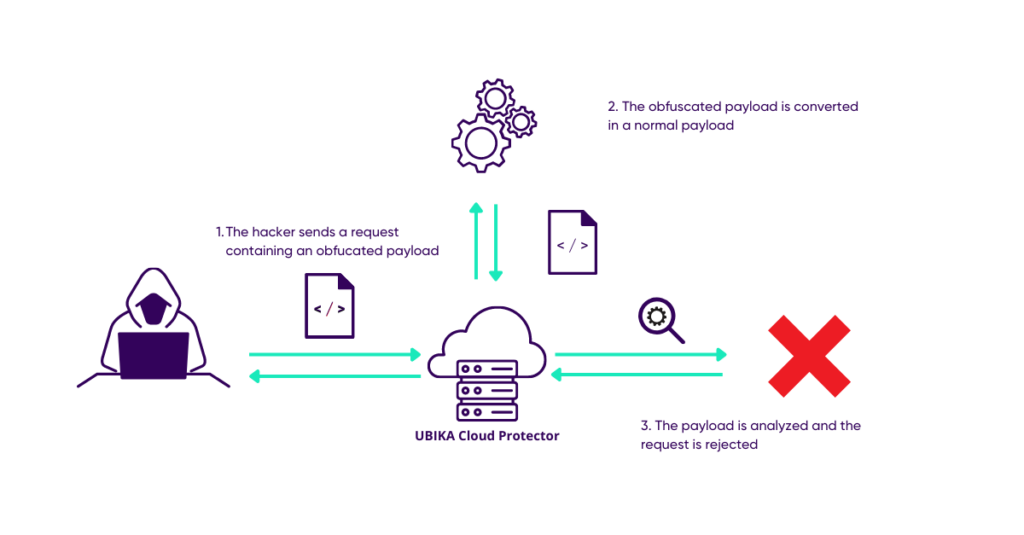
2. Computer obfuscation attack
In this second example, the attacker sends the same attack but obfuscated (using the techniques we will see below) so that the algorithms cannot draw any reliable conclusions.
Here, the web application firewall, not being designed to detect obfuscations, will let the attack through and the server may then be compromised because the web application firewall will not have known how to distinguish a real request from a fake one.
What are the different types of obfuscations?
Multiple obfuscation techniques exist and differ from one language to another. Let’s mention some examples:
Code obfuscation, which language?
1. Double encoding
In a web request (HTTP request), each character corresponds to a hexadecimal number and can be represented as %XX, where XX is the number in hexadecimal e.g. %2F representing the “/”
To avoid certain filters it is possible to encode the “%” sign, so the “/” which gives %2F in hexadecimal, can be encoded as %252F.
The double encoding can also be encoded, we speak then of multi encoding, that is used in particular to exploit Directory Traversal type flaws.
It is of course necessary that the backend is also able to handle multi-decoding for a vulnerability to be exploited.
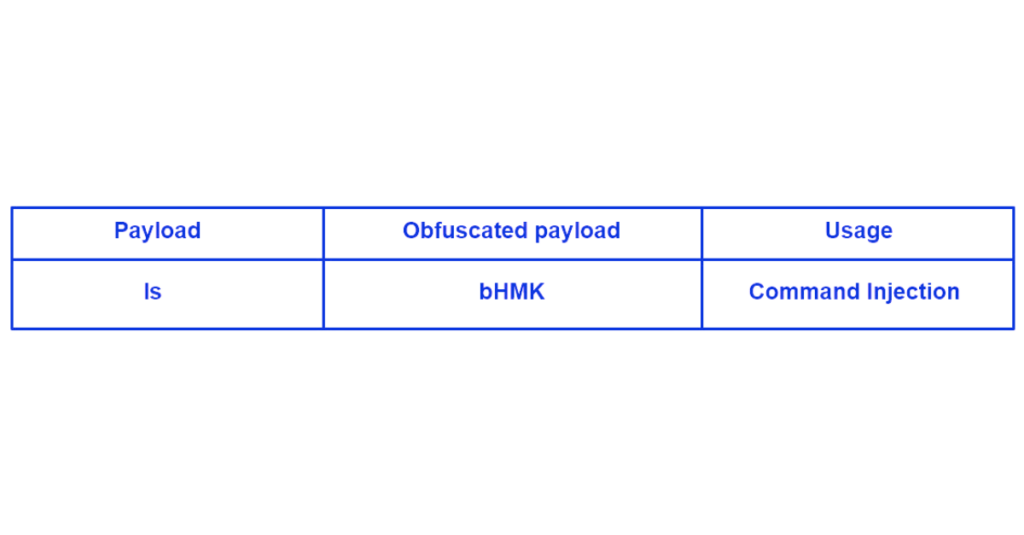
2. Base64 encoding
Base64 encoding is a process that can be used for different purposes. Let’s take an example with the command injection.
On a terminal it is possible to convert a command to base64, and then execute it in the following way:
![]()
If a web application firewall is only intended to filter certain commands, it will give in to this manipulation and can easily be bypassed using this method.
3. Properties of a language
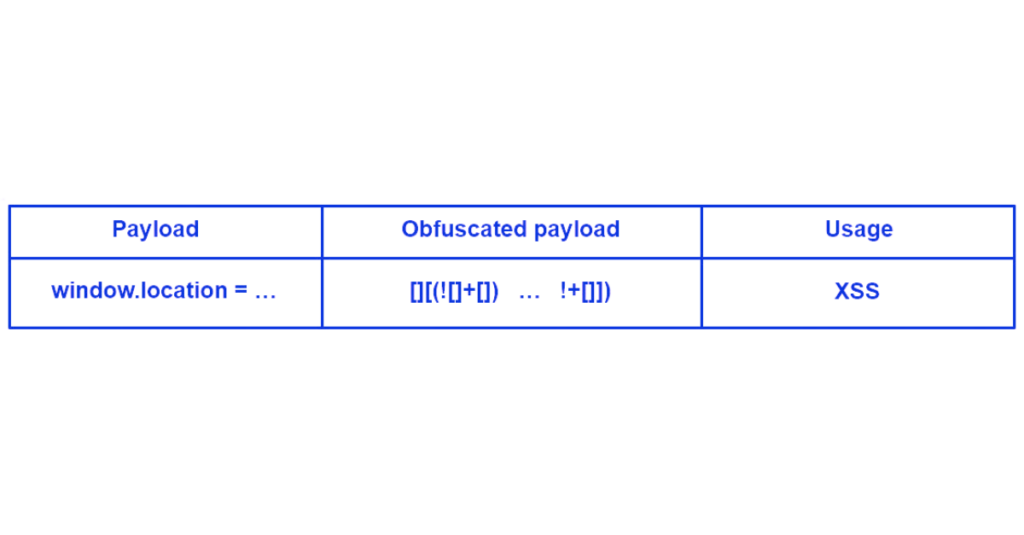
Other means of obfuscation exist, sometimes implemented directly in a language, an example can be Javascript with its atomic part.
This obfuscation technique is based on only a string of 6 characters: [, ], (, ), ! and +, and allows to transform Javascript code into a script incomprehensible to a human.
To obtain the simple letter “d”, it is necessary to use “[[][[]]+[])[!+[]+!+[]]”, so a code to exploit a XSS can easily go up to more than 20000 characters.
How does UBIKA Cloud Protector protect against computer obfuscation?
In order to avoid being trapped, UBIKA Cloud Protector uses normalization engines to identify obfuscation techniques before launching its analysis.
The engines used by UBIKA Cloud Protector can be called recursively and thus counteract multiple encodings.
Thus, the obfuscated parts of a request are decoded, analysed and sent to the different security engines depending on the attack pattern encountered.