SQL Injection
The family of Structured Query Language (SQL)injections groups together a large number of vulnerabilities that have in common the interaction with a SQL database.
The SQL flaws are present when the server uses user input without filtering it to run one or more SQL queries.
What are the different types of SQL injections?
Different methods of exploiting SQL flaws exist and adapt depending on what the server allows.
Among the most well-known:
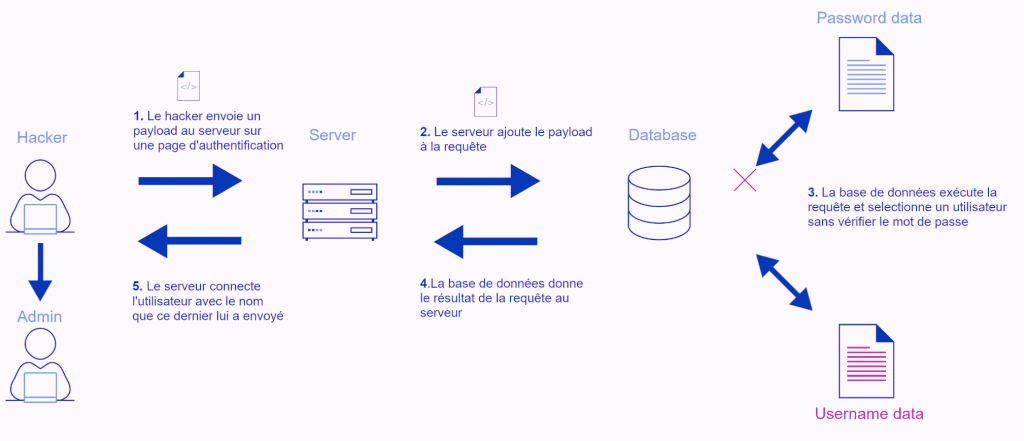
“Classic” SQL flaw (with ‘OR 1=1 -):
This is the SQL flaw par excellence, especially present on authentication forms, it allows to connect to any user account.
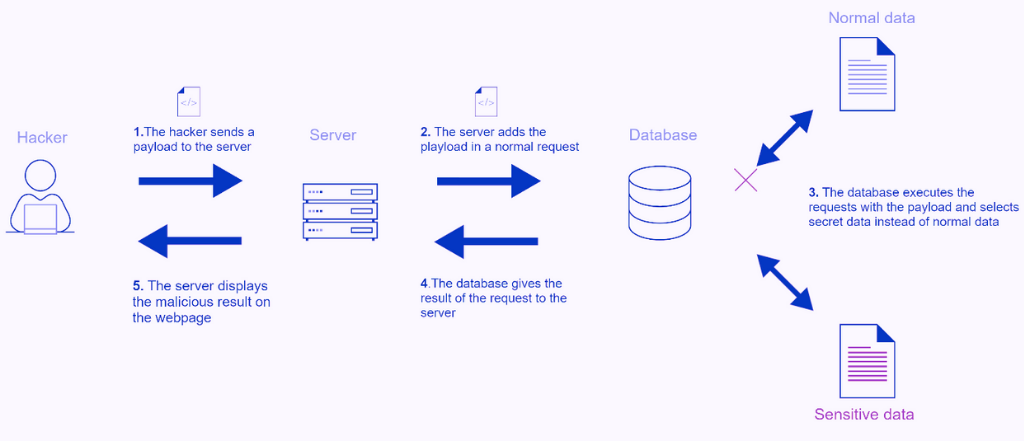
“Union-based” SQL query:
In SQL language, the UNION operator is used to merge the result of 2 queries, this adds the desired data to the data present in the first SQL query.
“Blind” SQL flaw:
Present when the retrieved data is not displayed on the screen, the attacker will use a condition allowing him to pause and will rely on the response time of the system to know if his injection is successful, this technique is used in particular to “brute force” the data we want to recover.
Many other methods of SQL injections, from the “Error Based” vulnerability that allows values to be displayed in an error message to the “Stacked Query” that gives the ability to perform any queries. It should be noted that databasesNoSQL also have their vulnerabilities.
Consequences of SQL injections
SQL injections cause three big problems:
Data recovery: Probably the most well-known problem related to SQL injections, with the ability to add custom queries, an attacker can recover any data present in a SQL database.
It is very common for databases to leak with users’ personal information (name, email, address).
This implies that great care should be taken with sensitive data that might be stored online.
Account theft: When an SQL injection is possible on a login form, it is very easy for an attacker to authenticate with an account that does not belong to him.
In addition to identity theft or data theft, it is the proper functioning of a web application that can be compromised if an administrator account is recovered.
Data corruption: Most dangerous case, exploited with Stacked Querry.
An attacker who has the ability to perform any queries on a SQL database can very easily modify or delete data.
In addition to the corruption that can be problematic for important information, this can lead to the same problems mentioned above: An attacker who can change a password is an attacker who knows the password.
Most websites store their content in a database, so if a hacker has access to it, he can practice defacing or publish fake news.
How to do SQL injection
Normal use of a search bar (PHP & MYSQL)
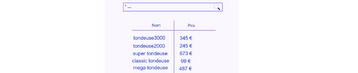
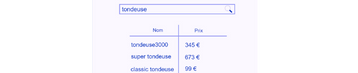
Let’s take the example of an online tool sales site. On one of the pages of the web application is a search bar allowing to find an item with its name and price.
Loris, the attacker will first perform a simple search to see the different models of lawn mower.
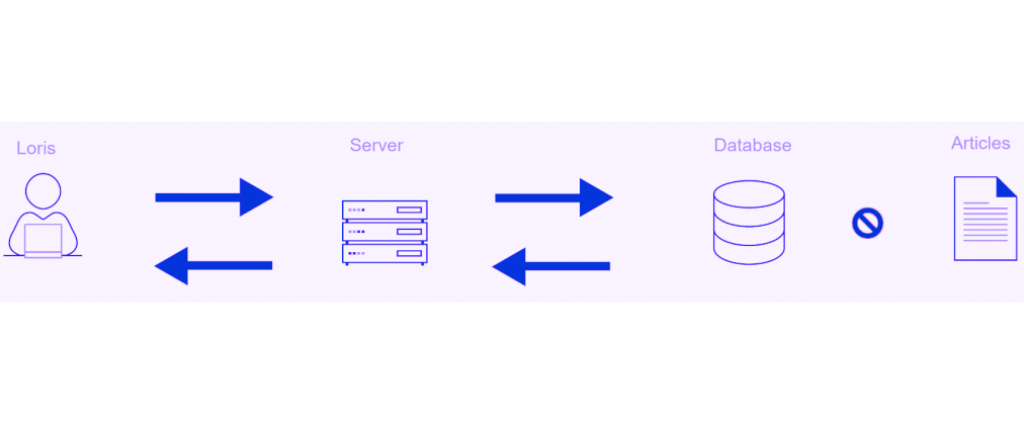
When he clicks the button the server will retrieve his input and insert it into a SQL query.
The server will then send this SQL command to the database which will execute it as code.
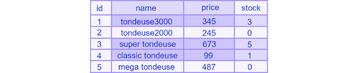
The latter will then fetch from the “items” table all the name and price of the items containing “tondeuse” in their name and with a stock greater than zero.
The server will retrieve this information and can then display it on Loris’ screen.
2. Testing an SQL injection
Loris sees that his search has been added to the url in the form “?name=tondeuse.”
He then decides to test if this parameter allows to enter SQL code.
He adds a ” ‘” which allows to open and close a string in SQL
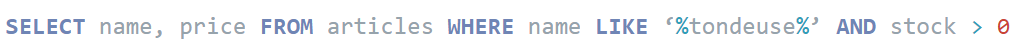
The database will then receive the following SQL command:
This query is invalid, as the second “%” ending up outside the string is considered a forbidden character
An error is then returned, “MySQL error: Invalid Syntax”
Loris now knows that a MySQL database is used.
In order to avoid this error Loris adds a MySQL comment to his query, this will allow him to remove the rest of the command thanks to the syntax ” ‘-”
This time the database accepts the query and will return all items, with the percentage acting as a wildcard, including those no longer in stock, with the condition removed


Loris only has to add his own requests to exploit the vulnerability.
3. SQL Injection Example.
Now that Loris has a valid query, the SQL injection attack can begin
His goal is going to be to retrieve the user passwords stored in the database
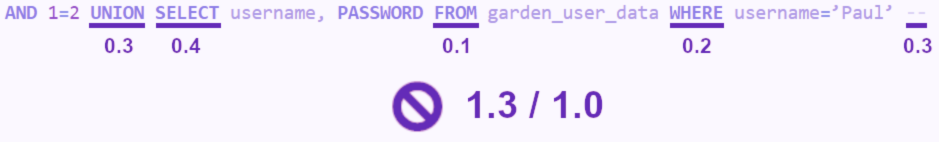
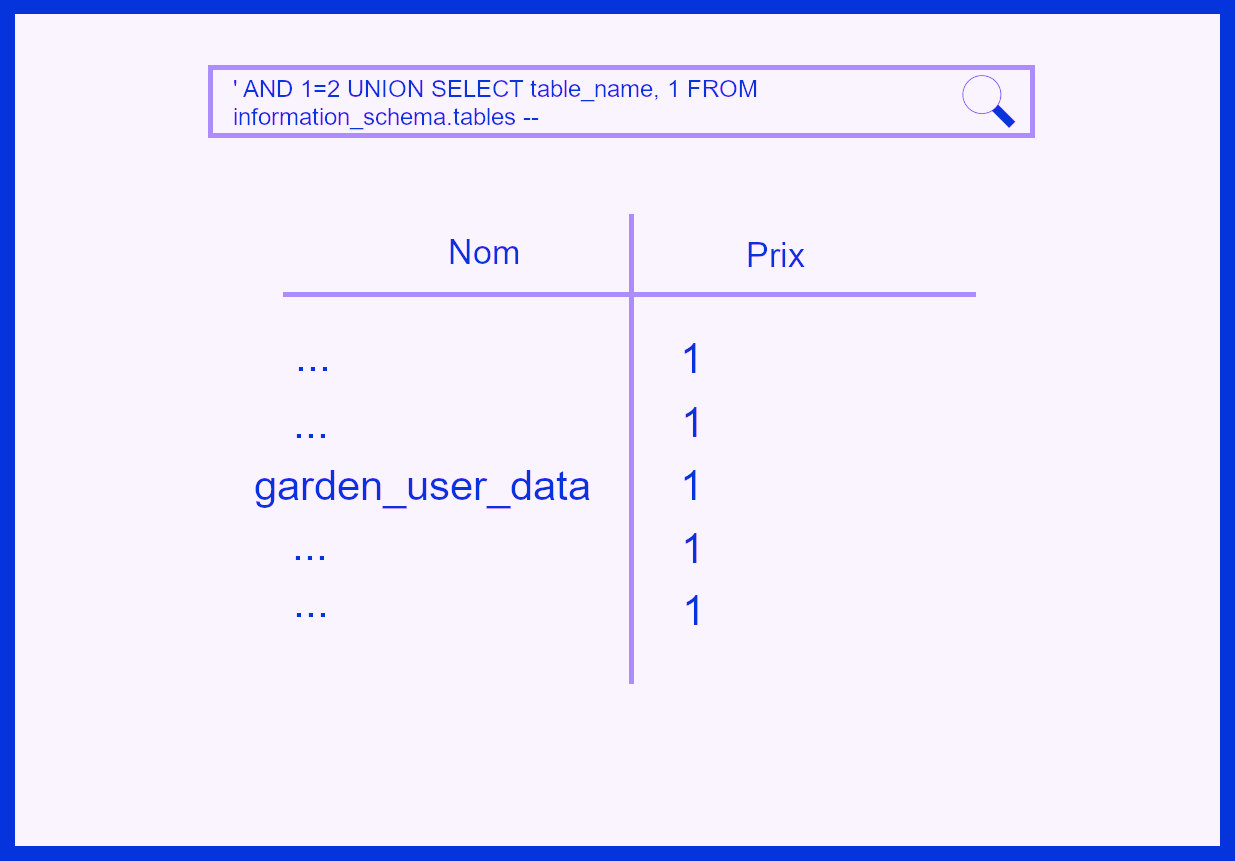
First of all, it needs to invalidate the current query so as not to retrieve the information on the items, for this, a simple “AND 1=2 –” will suffice.
The query will then try to retrieve the items if the condition 1=2 is validated, therefore, there will be no more results.
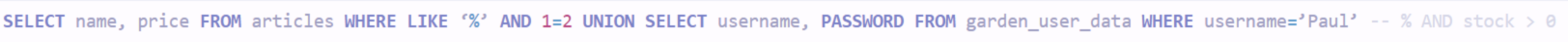
Loris will then use the UNION operator which allows to merge queries and add a SELECT allowing him to retrieve the name of the different tables.
With a few more SQL queries on different tables, Loris will discover that Paul is the site administrator, so he will retrieve his password.
So the password is cb28e00ef51374b841fb5c189b2b91c9.
Obviously passwords are never stored in clear text and this format seems to be that of an MD5 hash
The MD5 is an algorithm used to encrypt a text, you can’t reverse it but, some sites (https://md5decrypt.net/ for example) store a lot of text match – hash MD5.
Loris is lucky and finds the password associated with the hash: password123456
Loris only has to authenticate with the pair Paul / password123456 to get access to an administrator account.
In our example, the SQL injection attack was performed manually.
However, today there are tools such asSQLMap that make it easy to detect these attacks with pre-made scripts.



3. Example of SQL Injection
OWASP recommendation
The Open Web Application Security Project (OWASP) provides a guide to avoid SQL injections, here we will summarize the different options available to a developer.
Prepared querieswhich consist of writing SQL queries and adding the parameters to them later. This method allows you to insert parameters while avoiding escape character injection.
Uusing a “whitelist” (a list of allowed values) allows you to restrict the user’s scope of action and accept only upstream parameterized values
Escape user input remain an effective way to avoid any escape characters
UBIKA Cloud protector vs SQL injections
To avoid different types of SQL injections, UBIKA Cloud Protector provides several tools:
The “Blacklisting” used on all protection levels:
If UBIKA Cloud Protector detects a pattern typically used to exploit a SQL flaw, the query will be immediately blocked and redirected.
“Scoring List”active on Advanced and High levels of protection:
UBIKA Cloud Protector will analyze the request and increment a score as malicious patterns are encountered. At the end of the analysis, if the score is above the allowed limit the request is blocked and redirected. This method has the advantage of being much finer and avoidingfalse positives.
Now that Loris has a valid query, the SQL injection attack can begin
His objective is going to be to retrieve the users’ passwords stored in the database
First of all, it needs to invalidate the current query so as not to retrieve the information on the items, for this, a simple “AND 1=2 –” will suffice.
The query will then try to retrieve the items if the condition 1=2 is validated, therefore, there will be no more results.
Loris will then use the UNION operator which allows to merge queries and add a SELECT allowing him to retrieve the name of the different tables.
With a few more SQL queries on different tables, Loris will discover that Paul is the site administrator, so he will retrieve his password.
So the password is cb28e00ef51374b841fb5c189b2b91c9.
Obviously passwords are never stored in clear text and this format seems to be that of an MD5 hash
The MD5 is an algorithm used to encrypt a text, you can’t reverse it but, some sites (https://md5decrypt.net/ for example) store a lot of text match – hash MD5.
Loris is lucky and finds the password associated with the hash: password123456
Loris only has to authenticate with the pair Paul / password123456 to get access to an administrator account.
In our example, the SQL injection attack was performed manually.
However, today there are tools such asSQLMap that make it easy to detect these attacks with pre-made scripts.