Anti-DDoS protection: choose UBIKA
Recognizing and mitigating distributed denial of service (DDoS Attacks) is a major challenge today. Companies, whether very large, medium or small, can all be scapegoats when it comes to such attacks. Some specific actions can boost your company’s overall security posture and make it strong enough to defend your business against DDoS attacks.
Analyze your website traffic
First of all, you need to familiarize yourself with the website traffic so that you can notice alarming signs such as your website being inaccessible for a long period of time or irregular spikes in traffic. Continue to check for existing security vulnerabilities in your system. If you find any, make sure to remedy them immediately.
Go for a decent operator strategy
You must have a decent network operator strategy. Since it targets the network, you can’t handle volumetric attacks with software alone. You need reliable operators who can mitigate the attack before it even reaches the server. There are experienced ISPs on the market that can reroute and eliminate the problematic portion of your traffic before it even hits your network. They will make sure that only the legitimate portion of the traffic reaches your servers.
Have a large network
Having a large network with plenty of capacity can provide you with more bandwidth to contain sudden surges in traffic. Of course, it’s not always possible to rent a huge network or scale it up due to the high costs, especially when attacks become colossal, but at least it will buy you time to prepare the mitigation response. For example, when the Mirai botnet hit famous journalist Brian Kreb’s blog, the only reason the provider was able to primarily fend off the attack was its large bandwidth. Cloud-based service providers can give you that advantage.
Formulate a contingency plan
Formulate an emergency response plan carefully and in advance. Delegate responsibilities within your IT security teams and contractors to reduce their response time following an attack. Also, ensure that your data center or the one managed by your contractors is prepared for such an incident.
Combine multiple security technologies
Operators must use multiple security technologies, in conjunction, to stop a DDoS attack. Rohde & Schwarz Cybersecurity leverages innovative technologies from Arbor Networks to detect SYN flood attacks, UDP flood attacks, amplification attacks, spoofed IP addresses and more.
As a last resort, your carrier can blackhole a few target IP addresses and modify the IP addresses in the background. This allows him to remove the malicious DDoS traffic and put it out of sight, hence the name “black hole”. This strategy protects the remaining assets in your infrastructure that are not directly under attack, but there is a downside to this. Because it blocks both legitimate and fake traffic, blackholing should only be used when other strategies are not working as intended.
Communicate effectively in the event of an attack
Finally, in case of an attack, you need to communicate both internally (hosting provider) and externally (customers) about the attack. So prepare a complete list of your contacts as well. Quick communication will reduce the number of complaints by phone, email, social networks, etc.
Ask for your 14 free days
Increase your vigilance with UBIKA’s DDoS protection architecture
Use an anti-DDoS firewall for more security
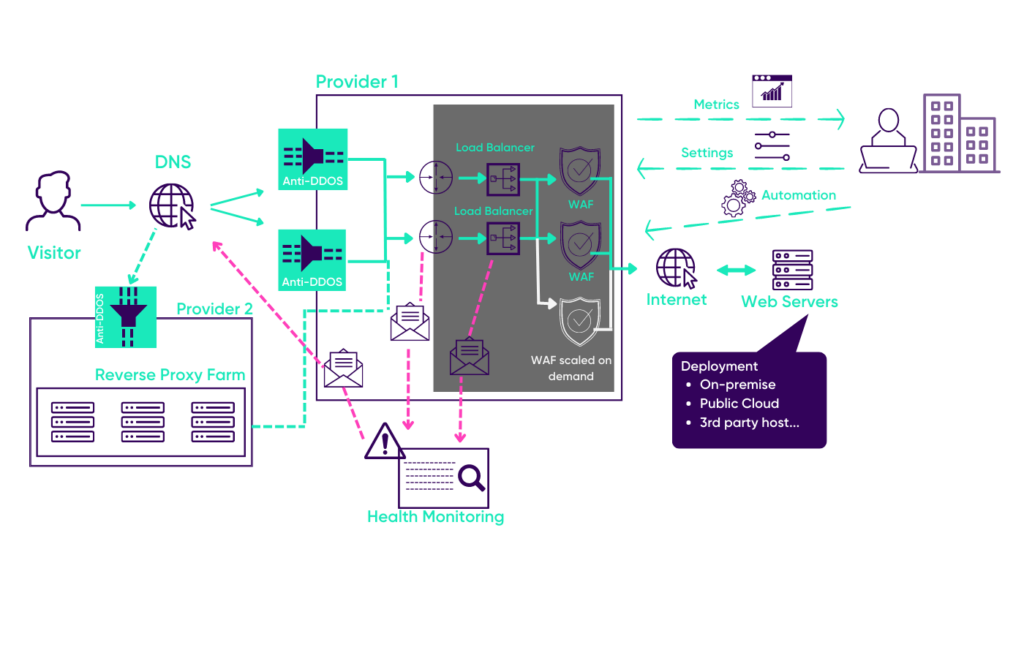
A SaaS web application firewall (WAF as a service) is one of the best ways to fortify your web applications against a DDoS attack. To set up a WAF, you can use UBIKA Cloud Protector, which is a highly scalable SaaS solution and easily adapts to your web traffic peaks. This scalability aspect is important to counter DDoS attacks. Most importantly, you benefit from carrier-grade anti-DDoS technologies as a first line of defense, even before the WAF. The Enterprise version’s DDoS protection architecture helps you by providing elasticity and convenience, even in the face of DDoS attacks. The client uses the Internet via DNS to access the web server. The DNS reacts by redirecting the traffic to the UBIKA Cloud Protector infrastructure. This SaaS solution is hosted by a provider that has anti-DDoS capabilities against common volumetric and application layer DDoS attacks. It supports inbound traffic and allows the customer to automatically scale up as soon as they reach a peak in their web traffic.
It supports multi-vendor deployment based on your needs. When customers have a traffic spike with a multitude of requests leading to a DDoS attack, and the first provider is unable to contain it, then the monitoring feature directly addresses the unwanted DDoS traffic to provide another layer of DDoS protection with another provider. And just like that, within minutes, an additional layer of defense is created for the customer.
Customers can directly use the graphical user interface (GUI) to secure their website, configure it and then automate it. They can apply a virtual patching solution (blacklist/blacklist of templates specific to their applications) to fix new vulnerabilities and common exposures (CVEs) with this SaaS-based WAF solution. They also have visibility into security incidents through various metrics in the comprehensive dashboards.
DDoS protection architecture
Read the article on DDoS WAF to learn more about the different techniques for protecting against DDoS attacks. Want the right solution to stop the next DDoS attack on your organization? You can contact us to get help from our experts.