DDDoS attack: an organization's worst nightmare
DoS and DDoS are common attacks that can make your server unavailable, if not taken seriously. In both attack scenarios, the basic principle is that cybercriminals deprive legitimate users of the service they need by making your system inaccessible. In the following sections, we will understand their main differences, the impact, the reasons for DDoS and the types of attacks.
Denial of Service (DoS) attack
In this attack, the attacker makes a massive number of requests (UDP or TCP protocol packets) to choke the victim’s server, with fake IP addresses. Gradually, all the resources of the attacked server (CPU, memory, etc.) are consumed. This is a common type of Denial of Service (DoS) attack, called “flooding”. There are also other forms, such as application denial of service, where cybercriminals send a server bug in a legitimate packet specifically designed to make the specific target unavailable. The principle of the denial of service (DoS) attack is to deny the user normal access to the host server and disrupt the normal operation of the system. When legitimate users can no longer access the website, it causes the server to fail.
Distributed denial of service (DDoS) attacks
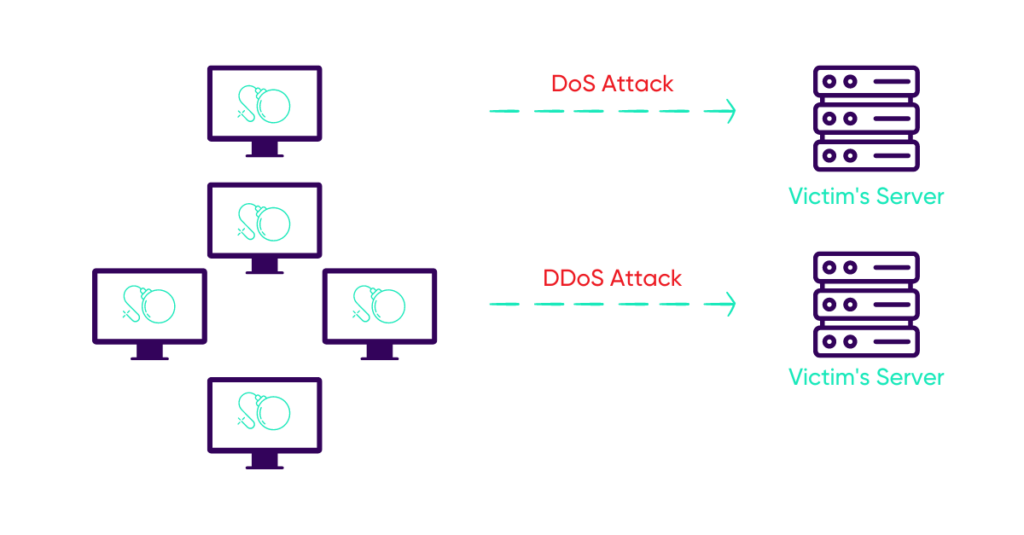
The number of distributed denial of service (DDoS) attacks continues to increase every year. While DoS is an attack between two individual machines, DDoS uses a group of machines coordinated at different locations (botnet) to attack the host. Hence the name “distributed”. This makes it more difficult to detect and block such attacks due to the bombardment from multiple sources in such a short time frame.
For the hacker, it is cheaper and easier to conduct a denial-of-service (DoS) attack.
DoS attack vs DDoS attack
What are the consequences of a DDoS attack? What are the specific targets?
The DDoS attack is faster and its intensity on the host server is much more critical and devastating. If your website stops working for too long, you risk losing more than your network connection, your valuable customers to competitors. You will lose your SEO ranking and your internal links. Not to mention the time needed to revamp your website and the financial consequences on your income. It could also damage your overall reputation in the marketplace and you may have to close your business for good.
As a service, the botnet usually targets relatively large sites and government agency websites. Online business sectors are a primary target of these DDoS attacks. If you have a thriving website, you will probably be the target of a DDoS attack at some point.
Who is conducting DDoS attacks and why?
Many hackers may form active groups to conduct DDoS attacks to express their opinions on a certain topic (politics, ethics, etc.) or to avenge an organization. Sometimes, people who are part of organized criminal groups do it to get a huge ransom.
Today, DDoS hackers are available at low prices on the dark web. Sometimes, companies hire these attackers and launch such attacks, to disrupt their competitors’ services and redirect traffic to their own website.
There are also times when attackers conduct such attacks just to show their skills.
Types of DoS and DDoS
There are two types of attacks.
Volumetric attacks
The attacker consumes all bandwidth to create network congestion with massive volumes of traffic, so that legitimate clients cannot access the specific target network. Most DDoS attacks are volumetric. Their volume can range from 20 gigabytes per second to 2 terabytes per second.
Application layer attacks
The attacker takes advantage of programming errors in the application and attacks the application layer or layer 7 of the OSI model. They tend to diversify these types of attacks to maximize their impact on the specific target.
Examples of specific attacks
SYN flood
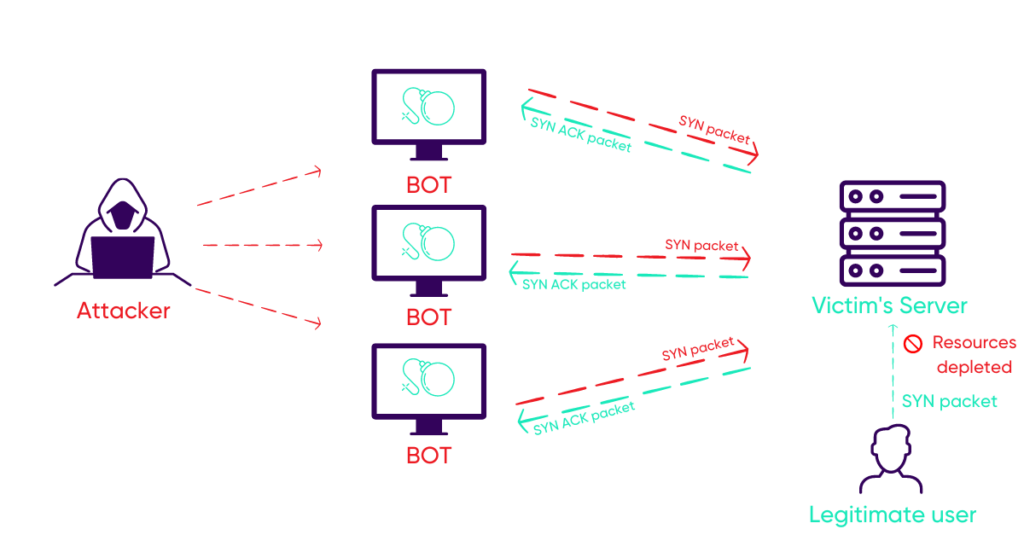
In this volumetric attack scenario (Figure 2), the perpetrators are not trying to exploit a security flaw on your website, but to cause it to break with a high volume of requests. They flood the specific target with multiple synchronization (SYN) packets from different machines simultaneously. The victim sends back legitimate acknowledgement packets (SYN-ACK). However, the attacker does not send an ACK packet in response to complete the three-way handshake, and makes the victim wait until the victim’s server exhausts all its resources. This results in a significant drop in the performance of the victim’s web server.
Figure 2: SYN flood attacks
Amplification attacks
The goal of an amplification attack is to use an amplification factor that maximizes the possible impact. Attackers use a slightly different technique (Figure 3) to cripple the victim’s network bandwidth by widening the outbound traffic flow. They manipulate open domain name system (DNS) servers by sending fake small queries (with the IP address of the specific target). The server mistakes the target machine for the source of the requests and sends it an amplified response message. DNS amplification is a popular example of an amplification attack. However, not all amplification attacks exploit the DNS. The attack can also target a router. For example, the Smurf attack is another type of amplification attack that relies on the router serving a broadcast network.
Figure 3: Amplification attacks.
Slowloris attack
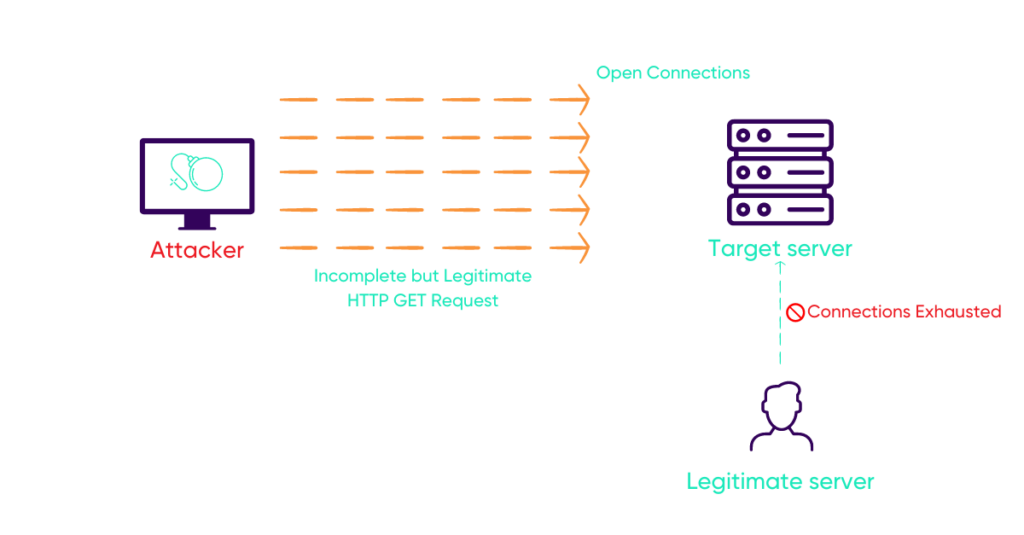
Slowloris is an application layer attack in which the cybercriminal periodically sends incomplete but legitimate HTTP GET requests to the targeted web server. In this way, it keeps the connections open and slowly and meticulously eats up the web server’s connection sockets, thus jamming all other legitimate requests.
Figure 4: Slowloris attack
How to tell if your site is under DDoS attack
In addition to hacker pressure, there could be several other signs of a DDoS attack. For example, when customers complain that your website has been inaccessible (loss of network connection) for an extended period of time or if you observe an irregular spike in website traffic in your logs. It is indeed hard to tell, as the latter could also be due to legitimate requests.
Protect yourself against DDoS attacks
The last notable DDoS attack in 2020, the AWS attack, lasted nearly 3 days and peaked at 2.3 terabytes per second. DDoS attacks are undoubtedly a significant security issue for your business. Therefore, you need to monitor your system thoroughly, adopt good practices, prepare with a powerful web application firewall Anti-DDoS option and develop a better global defense system to mitigate a DDoS attack. Don’t wait for your first attack! Do it now, before it affects your customers and your brand image!