How to prevent exploitation of Path Traversal vulnerabilities?
What is a Path Traversal/ Directory Traversal flaw?
The Path Traversal, or Directory Traversal attack is an attack affecting the server side of web applications.
Although not clearly stated in the OWASP Top 10, the vulnerability can lead to a flaw present in this top: Broken Access Control (A5:2017-Broken Access Control | OWASP)
This vulnerability allows a user to have access to data or functionalities outside of their scope of action, for example, the fact that an ordinary user can modify the profile of any other user when this action is supposed to be reserved for administrators.
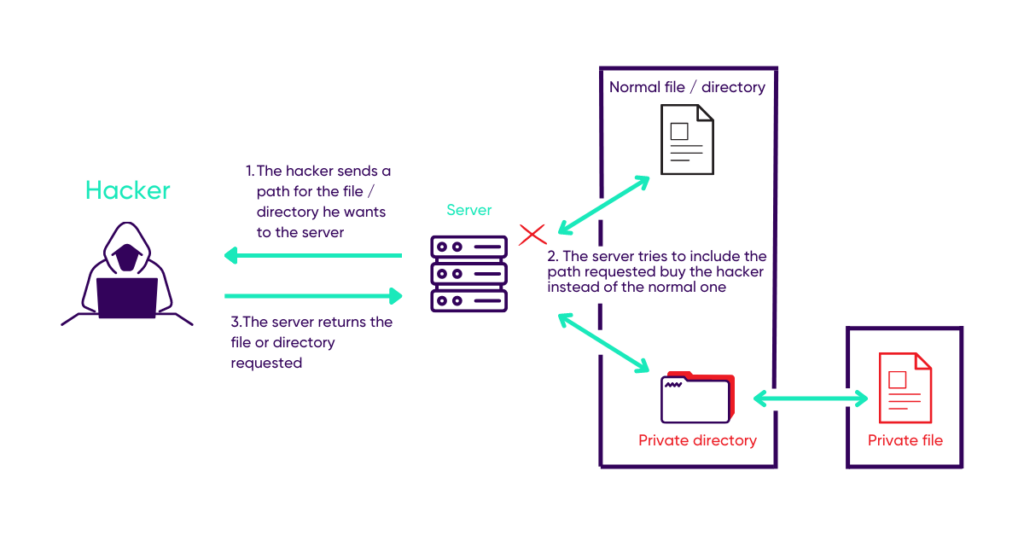
The Path Traversal / Directory Traversal vulnerability consists of manipulating HTTP parameters, most often using GET. The GET request allows to modify the url, in order to include and have sensitive folders or files in a web page.
IMAAAAGE
Consequences of a Path Traversal / Directory Traversal attack (Directory path traversal attack)
The Path Traversal flaw has some consequences.
- Data infiltration: if the attacker succeeds in including folders containing sensitive files he will then be able to see their names and display them.
- Access to restricted functionality: If the attacker manages, for example through a GET or POST request, to include an administrator page he will then have the ability to perform actions that are not normally possible at his privilege level.
This flaw is particular because it can also lead to the exploitation of other flaws:
- Recovery of the site’s source code: In the case of a server running with PHP, the attacker can include the source code of the various pages and analyze them for other flaws.
- Server analysis: By including files such as .htaccess, the attacker has the possibility to understand how the server is configured.
The consequences of a path traversal flaw depend very much on the server configuration.
What is a Path Traversal flaw?
The path traversal, or directory traversal attack is an attack affecting the server side of web applications.
Although not clearly stated in the OWASP Top 10, this vulnerability can lead to a flaw present in the top 10: Broken Access Control (A5:2017-Broken Access Control | OWASP)
The latter gives the possibility to a user to have access to data or functionalities outside his field of action, for example, the fact that a normal user can modify the profile of any other user while this action is supposed to be reserved for administrators only.
The path traversal vulnerability consists of manipulating HTTP parameters, most often in the query string, which means modifying the URL, in order to include sensitive folders or files in a web page.
How to exploit a Path Traversal vulnerability?
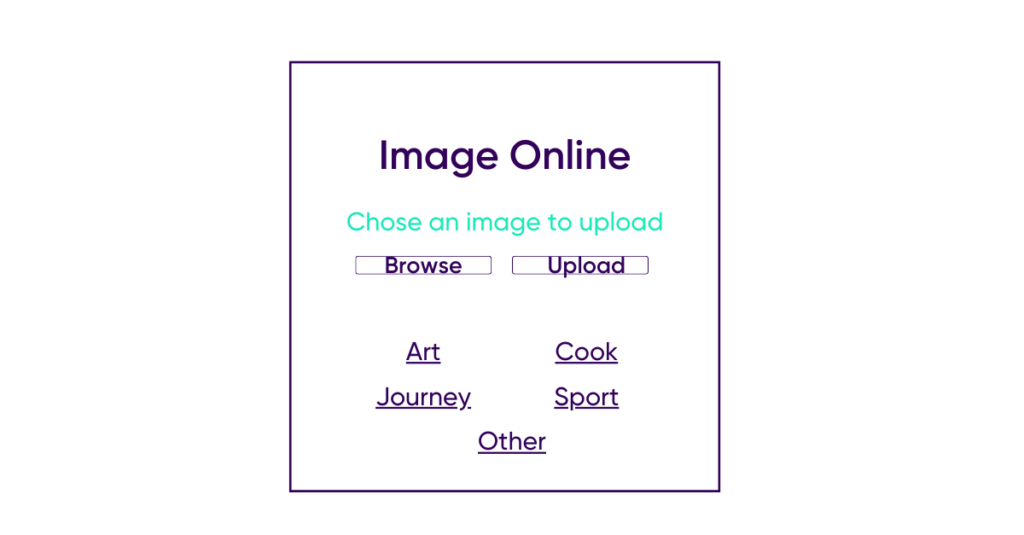
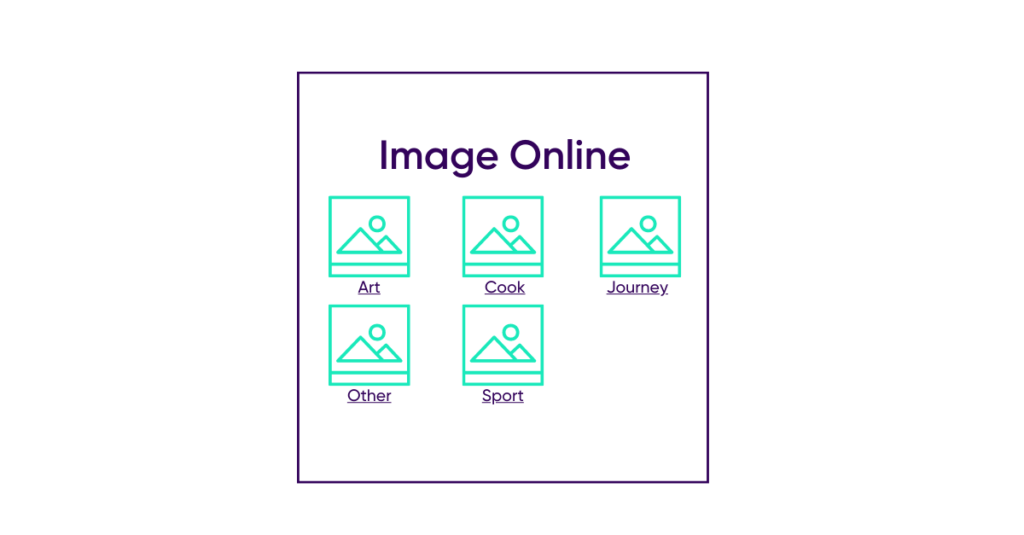
1. Normal use of an online photo gallery
Consider a site that allows you to upload images by assigning them a category and view them.
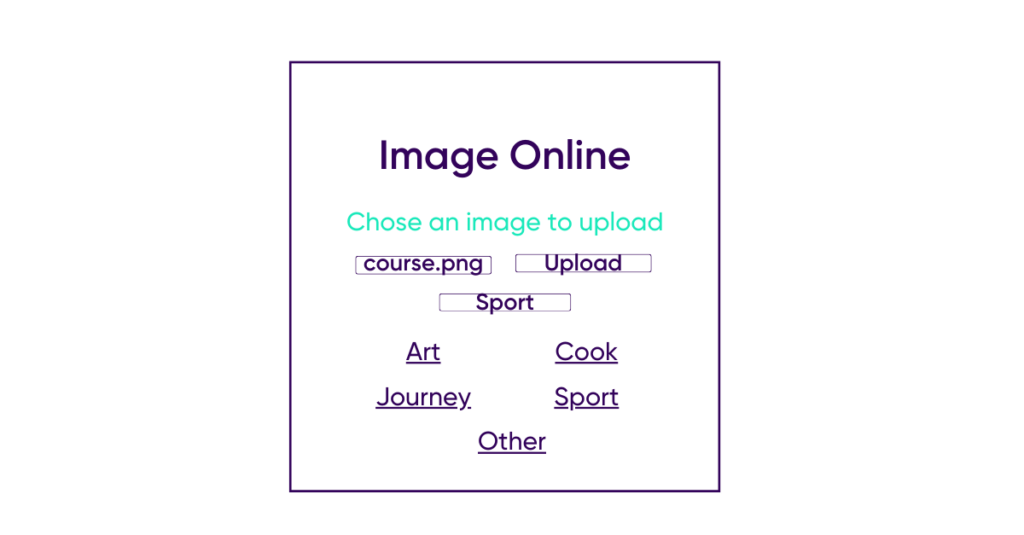
Loris, our attacker will be able to select an image and assign it a category and then send it to the server.
Loris will then click on the “Sport” category that corresponds to the image he added
The url of the page then becomes
http://www.image-online.com?path=sport
The different images of this category will be displayed
2.Path Traversal Test
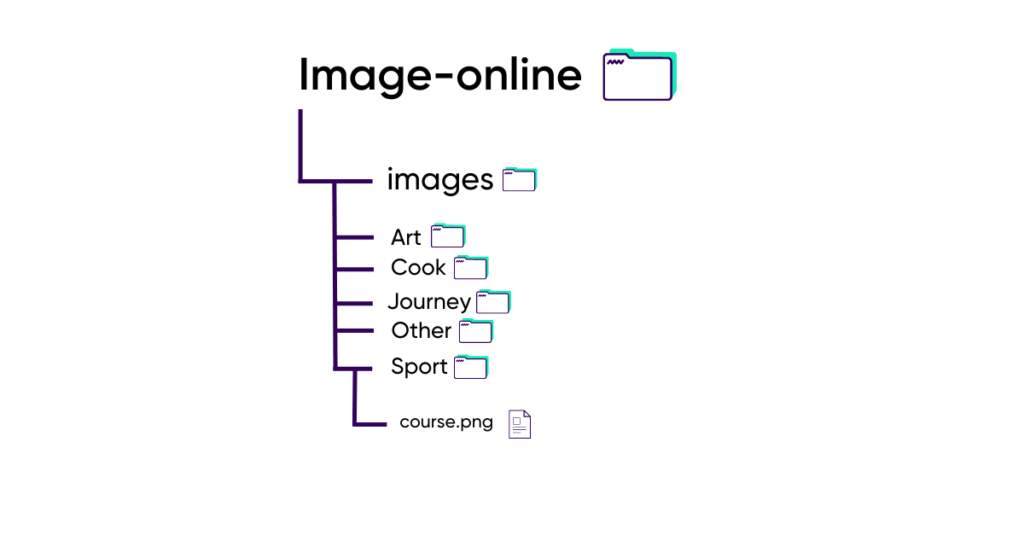
Loris will now go to page “Sport” and modify the URL by changing “sport” of the path variable by “./ “.
“./” indicates the current folder.
http://www.image-online.com/?path=./
The page that appears shows the different categories that exist for an image:
Loris now knows that he is in the root folder of the different categories;
He has a good understanding of how the server works.
3.Exploitation of the flaw
Loris’ goal is to find out how to use this path traversal to perform actions as an administrator.
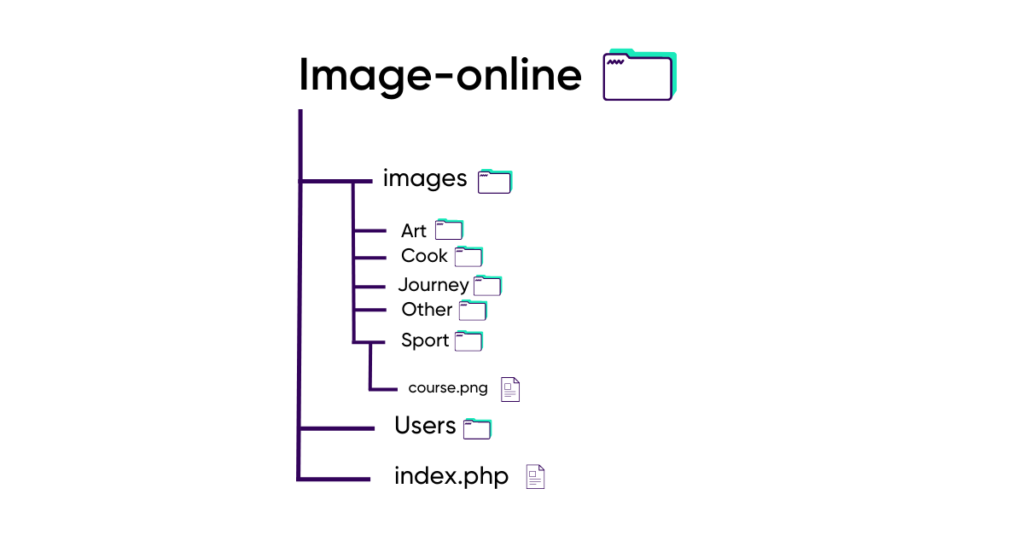
The tree structure he currently knows is the following:
By taking only the path variable and changing its value by ../, which indicates a backward movement in the tree, Loris ends up with different file and folder names.
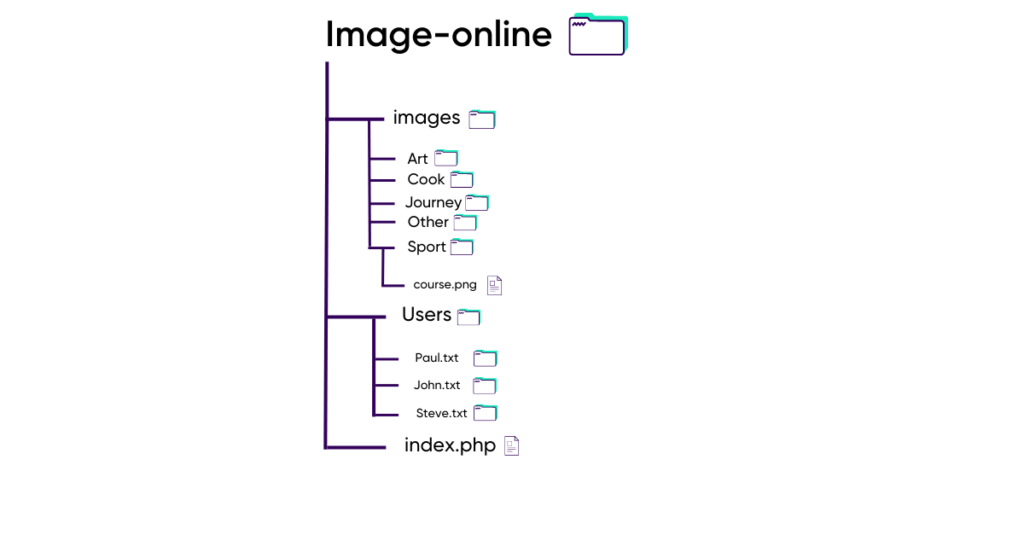
We can see a “Users” folder and by replacing “../” by “../Users” Loris finds himself with a list of files that seem to relate to different users:
By changing the URL of the page by http://www.image-online.com/Users/Paul.txt, Loris recovers all his information stored in hard disk, including his password.
He only has to authenticate himself with his information to have an admin account.
OWASP recommendations in Path Traversal vulnerability prevention
The Open Web Application Security Project (OWASP) provides a guide to guard against Path Traversal vulnerabilities, here we will summarise the different options available to a developer.
- Avoid using user input to include local files: This prevents a user from being able to test a Path Traversal vulnerability.
- Accept predefined values: This can be enforced by a series of conditions in the server-side code.
- In this case it is necessary to escape user entries in order to avoid path traversal patterns. (such as “../” for example)
UBIKA Cloud Protector vs Path Traversal
In order to prevent the exploitation of Path Traversal vulnerabilities, UBIKA Cloud Protector has an effective method:
- Malicious pattern detection: UBIKA Cloud Protector automatically detects patterns used during path traversal in order to block and redirect malicious requests
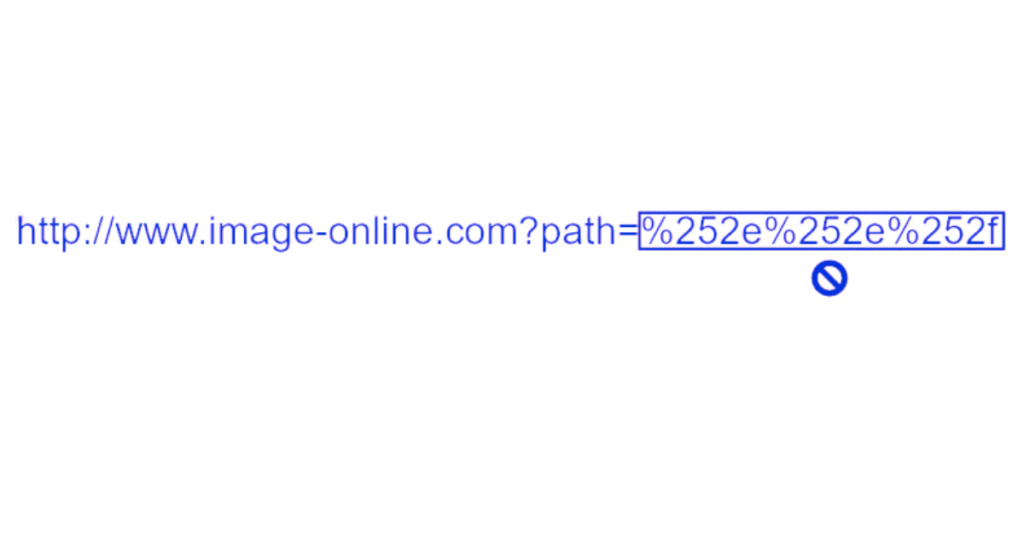
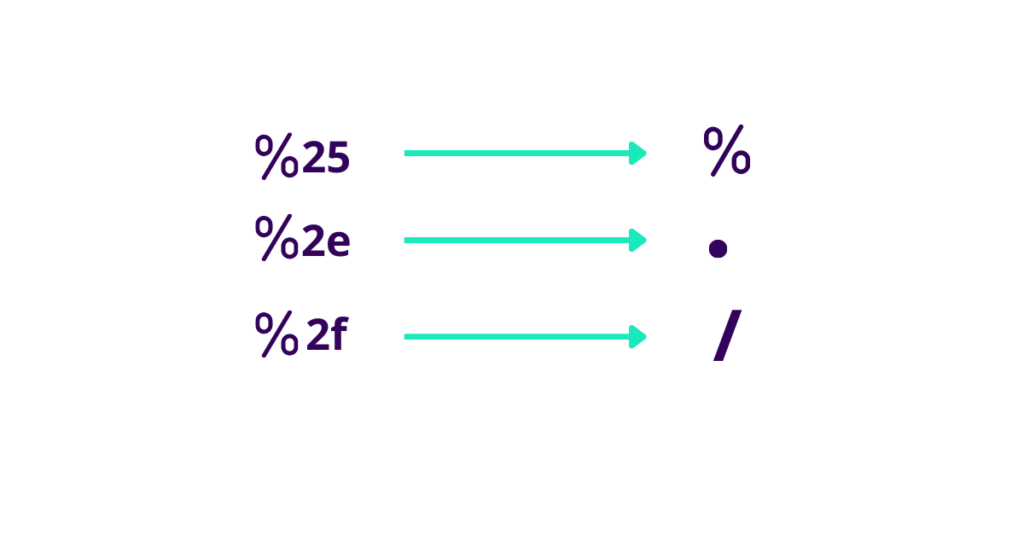
With the translation above we can understand that %252e%252e%252f will give %2e%2e%2f and then ../