Botnet DDoS: preventing your network from turning into a zombie
Botnet definition
Nowadays, botnets have become one of the most widespread and constantly evolving dangers in cybersecurity. A botnet is a group of computers connected to the internet that perform a task such as cybercrime. The hacker then infects the devices with malware to gain access to the devices and gain absolute control.
How to create a DDoS botnet
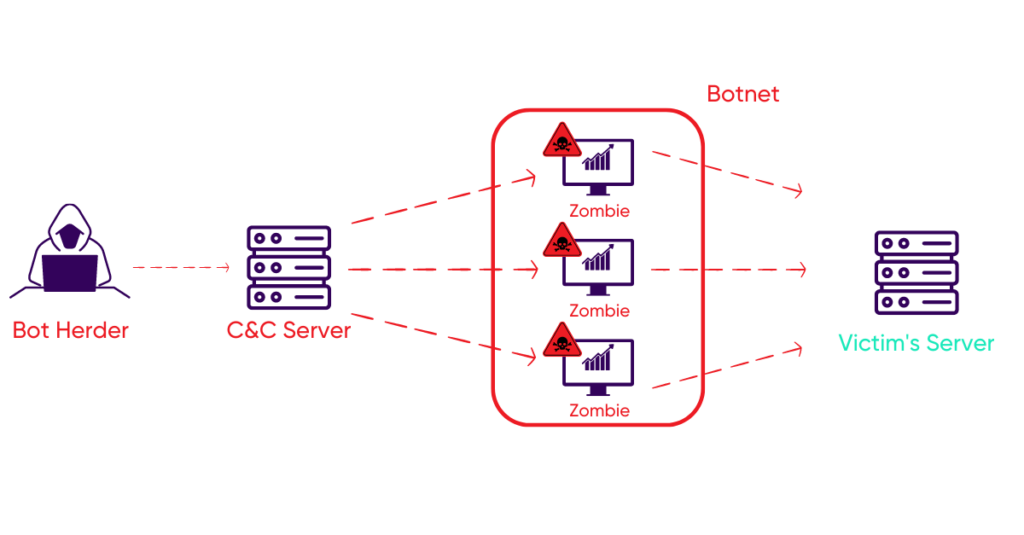
In the past, hackers or botnet owners (called bot herders) used to create their own botnets with a command and control (C&C) server (Figure 1). Botnets are also called zombies because they perform malicious actions in a robotic manner. The owners of these bots often tend to exploit a vulnerability in an application or website. They install malware such as Remote Access Trojans (RATs) to infect the device and take it under their control (and thereby reach your personal data). They can also perform phishing operations to spread malware via email and get into the user’s device when the user clicks on a spam message. Then, hackers organize the devices into a network of computer bots to serve their bids by carrying out large-scale attacks.
Together, the power of these bots could be equivalent to a supercomputer. With such an army of bots at their side, the hacker now has more resources, with greater computing power and can orchestrate attacks on a larger scale than was possible with a single machine.
Figure 1: DDoS botnet
Attackers use this botnet to launch Distributed Denial of Service (DDoS) attacks to extort money from businesses, spam to steal money, cryptocurrency mining, credential stuffing, phishing, etc. Sometimes attackers use a botnet attack simply to distract the victim while they plan a more sophisticated cybercrime. They may also rent out their botnets.
DDDoS as a Service
Today, with the emergence of DDoS as a service (also known as Booter services), attackers create botnets and rent them to others to commit DDoS attacks. They can be rented even by inexperienced novices, using web services, which look like legitimate web applications. They allow customers to sign up, choose an appropriate package to plan their DDDoS attack based on their budget, attack the target vector or profile, and place an order with a few clicks. Some of these services even have customer loyalty programs, like any other legitimate business platform. Not to mention that they market their services on platforms like YouTube. The growth of this sector on the dark web is a key factor in the growing innovation and competition among hackers.
Price of a DDoS Botnet
The price of a DDoS as a service can depend on the target (for example, hackers may charge more to government institutions) and also depends on the type of protection the target organization may have in place. The different scenarios involved in a DDoS attack and the resources needed to carry it out are also determining factors. To give an idea, a DDoS attack lasting 10,800 seconds costs the customer about $20 per hour. It is inexpensive for the customer but can be devastating for the target.
IoT botnet DDoS
Internet of Things (IoT) devices have many advantages. Today, with the increasing adoption of IoT devices, the new trend for hackers is to exploit and infect IoT connected devices such as smart home appliances, camera IP addresses, baby monitors, connected cars, medical devices, etc. These devices represent a huge opportunity for hackers as they can exploit their weak security measures and poor password practices to integrate them into their botnets. The security aspect must be considered when developing IOT.
The biggest DDoS attack from a botnet: Mirai
Mirai, which is a self-propagating malware, was a hot topic in 2016. Mirai botnets were used to launch a series of some of the largest DDoS attacks, exceeding 1 Tbps. The first attack was launched against French hosting company OVH. It was also used in an attack against the information security blog of well-known journalist Brian Krebs. It also attacked the servers of the DNS provider, Dyn, bringing down its sites including Twitter, Netflix, etc. These botnets tracked, penetrated and enslaved over 600,000 vulnerable IOT devices, such as surveillance cameras, etc. Since this infamous incident, several hacker groups have reused the mutated version of the same code to run their own Mirai botnets.
However, there are also good botnets. Researchers are allowed to create their own botnet machines. For example, Seti@home, where “Seti” stands for Search for Extraterrestrial Intelligence. David Gedye designed this project to use a set of Internet-connected computers that listen to radio telescope signals from space. This demonstrates how the power of a botnet can be harnessed for the good of humanity and not in the sense of the Mirai attack.
Nevertheless, you need to teach people to be more defensive and proactive by not opening untrusted emails or downloading data from untrusted sites. Implementing a strong security system with a SaaS web application firewall with DoS protection capabilities can prevent botnets from disrupting your network and keep it from turning into a zombie.