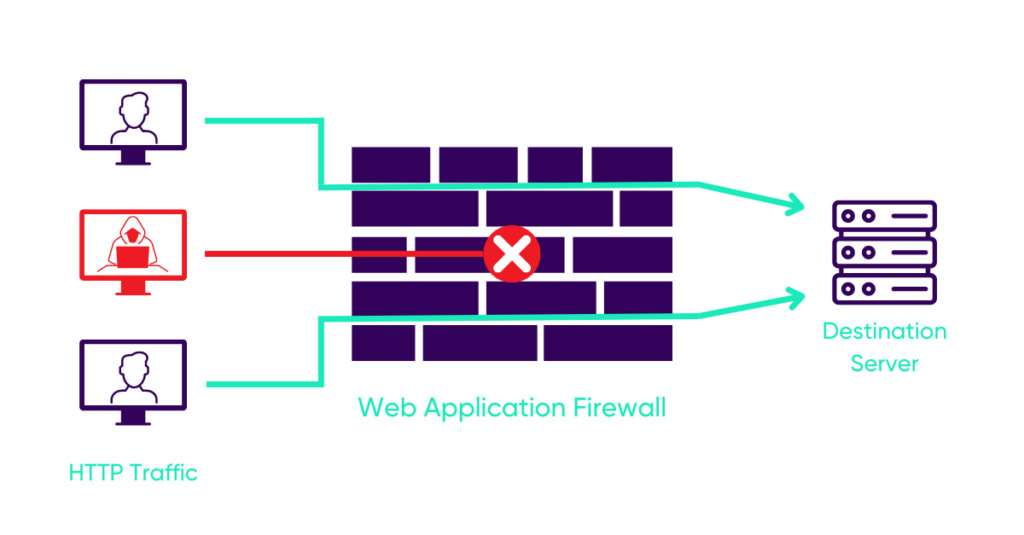
Web application firewall (WAF), an essential element of web security
Driven by teleworking, the adoption of SaaS (Software-as-a-Service) solutions in businesses has risen sharply in recent years. According to the annual study by the American company BetterCloud, this use increased by 1275% over the period 2015-2021 with an average consumption of 110 SaaS solutions per company. E-commerce platform, web application, API, web-services, these architectures are used daily and transparently by HR, marketing, sales and technical teams. Unfortunately, this use is also accompanied by an increase in cyber attacks targeting cloud environments. To prevent data being compromised or even exfiltrated, the use of a Web Application Firewall (WAF) has become an essential element of web security. What role does it play? How does it detect threats? Explanations.
Definition of a Web Application Firewall
A Web Application Firewall (WAF) is a virtual security tool designed to protect organisations from application vulnerabilities by filtering, monitoring and analysing hypertext transfer protocol (HTTP) and secure hypertext transfer protocol (HTTPS) traffic between web applications and the Internet.
How does a Web Application Firewall (WAF) work?
A Web Application Firewall (WAF) is an application firewall whose role is to filter malicious HTTP/HTTPS requests that may target web infrastructure vulnerabilities (CVEs) or development errors in the application layer. Located at the flow break between the visitor and the web server, the Web Application Firewall acts as a reverse proxy, distributing the legitimate request after analysis. UBIKA’s Application Firewall can be installed as a physical appliance (on-premise), in the form of a virtual machine (container or cloud image), in the form of a SaaS service or directly hosted on the marketplaces AWS, Google Cloud or Microsoft Azure with the Web Application and API Protection (WAAP) offering.
What type of web application can be secured by a WAF?
This technology is intended to be agnostic and integrates with any type of framework (gRPC), web server (Apache, NGINX, Microsoft IIS) or data exchange standard and protocol (WebSocket, GraphQL, REST, SOAP). By recognising cyber-attacks, the web application firewall can detect malicious behaviour such as a suspicious increase in the volume of requests (denial of service), the use of an IP affiliated to a botnet, or the pattern of one of the 10 main cyber-attacks in the OWASP repository.
How the application firewall detects and blocks OWASP repository attacks
Web infrastructures are one of the favourite targets of cybercriminals. To document and list the modus operandi, the Open Web Application Security Project (OWASP) developed by the OWASP Foundation publishes the ranking of the top 10 attacks that target web applications, websites and other APIs.
The OWASP Top 10 includes the following attacks in particular:
- SQL injection
- Cross-Site Scripting (XSS)
- Broken Authentication and Session Management
- Cross-Site Request Forgery (CSRF)
- Vulnerabilities in third-party components (WordPress Plugin, CVE)
For each of these attacks the web application firewall provides a solution.
SQL injection: By analysing HTTP/HTTPS requests, the WAF detects the patterns used, blocks the request and bans the sender’s IP.
Cross-Site Scripting (XSS): As with SQL injection, the WAF detects attempts to inject malicious JavaScript code, blocks the offending request and lets legitimate traffic through.
Broken Authentication and Session Management : Login and password communicated in the request, session ID exposed in the URL, deduction of the login based on information publicly available on the website (author name of articles…), the WAF detects attempts to bypass traditional authentication methods.
Cross-Site Request Forgery (CSRF): Based on a set of detection rules, the WAF detects and blocks any attempt to falsify cross-site requests.
Vulnerabilities in third-party components (WordPress plugin, CVE): It is commonplace for vulnerabilities to appear in third-party components of an application. Whether in the application libraries used by the apache web server, as was the case with the Log4j vulnerability, or through critical flaws in CMS plugins, WAF makes it possible to ensure a level of security even before systems can be updated.
Check out our article: How to protect your applications from the attacks in the OWASP Top 10.
How Web Application Firewall (WAF) detection complements Next Generation Firewall (NGFW) detection
The Next Generation Firewall (NGFW) and the Web Application Firewall (WAF) provide complementary threat detection. When the WAF analyses and detects threats targeting web environments, the firewall analyses and detects threats trying to enter and transit the company’s internal network. The WAF secures HTTP/HTTPS flows (protection of layer 7 of the OSI model) while the firewall analyses TCP/IP packets. Thanks to its threat detection component (IPS), the firewall analyses, detects and blocks threats using the Telnet, FTP, SNMP, DNS and SMTP protocols (layers 3 and 4 of the OSI model).
The WAF, a bulwark against Denial of Service (DoS) attacks.
The use of denial of service (Ddos) attacks has been increasing in recent years. Initially used to saturate the victim’s infrastructure with requests and render it inoperable, denial of service now accompanies ransomware attacks (Ransom DDOS or RDDoS) with the aim of demanding a ransom under the threat of infrastructure paralysis.
To detect and stop the attack before it hits the targeted infrastructure, WAF offers several features:
- Request rate limiting: By defining a maximum request volume threshold, the cybercriminal cannot saturate the protected asset.
- The use of blacklist and whitelist: By using generic detection rule templates (blacklist) and filtering rules based on how the API works (whitelist), known as positive security, this method allows the application firewall to adapt its detection and filtering policy.
- Threat Intelligence (CTI) and geolocation: Cybercriminals use botnets or zombie machine networks to launch their attacks. Based on an IP reputation database, the WAF detects and blocks a request sent from a malicious IP.
Discover how to defend against DDOS attacks in this specific article.
What is the role of a WAF?
Here are a few use cases:
- Protect your web applications
- Improve your API security strategies
- Detect and mitigate malicious bots
- Defending against DDoS attacks
- Integrating security into your DevOps approach
- Implementing a hybrid cloud & multi-cloud strategy
What action can a modern waf take?
- Develop security policies using our graphical workflow technology
- Enhance API security with additional engines
- Detect and mitigate malicious bots, to ensure legitimate traffic
- Avoid false positives with automatic and advanced resolution
- Adapt to IP Reputation, user behaviour and context-specific scenarios
- Define and customise dashboards for advanced monitoring and reporting.
How to choose a WAF? How to install a WAF.
Web Application Firewall On-Premise
The WAAP is deployed on corporate sites in the form of a hardware appliance or virtual machine to protect critical applications present within a corporate data centre. In this case, the data centre operator must be involved in configuration operations and software updates.
The company may also have an on-premises private cloud, in which case it will be able to control orchestration, scalability and other aspects. However, an on-premises WAAP suffers from the limitations of the private cloud.
Discover our WAF solution, UBIKA WAAP Gateway / On Prem Edition.
Cloud Web Application Firewall
WAAP is offered via cloud marketplaces that allow you to deploy an instance. This model reduces your initial investment and benefits from the latest security updates. A relevant model consists of combining a BYOL (Bring Your Own License) mode, for instances that are operational 24/7, with a Pay As You Go (PAYG) mode that encourages scalability. Cloud orchestrators use Terraform scripts to control scalability and capacity reduction. This makes it possible to deploy an Infrastructure as Code (IaC) approach that automates the entire process.
Here is the list of cloud providers on which our solutions are present:
- Azure – Web Application Firewall
- Amazon (AWS) – Web Application Firewall
- Google Cloud Platform – Web Application Firewall
- OVH – Web Application Firewall
- Outscale – Web Application Firewall
Discover our WAF solution, UBIKA WAAP Gateway / Cloud Edition.
Web Application Firewall in SaaS mode
WAAP is perfectly suited to a SaaS model, with deployment and maintenance provided by the publisher, without any installation operations by the customer. Simple to deploy and configure, all the customer has to do is redirect the application traffic to the hosted infrastructure. The supplier manages scalability, software updates and platform monitoring. This offering is often combined with DDoS protection to prevent volumetric attacks.
Discover our SaaS WAF solution, UBIKA Cloud Protector.
French Web Application Firewall
UBIKA solutions are designed, developed and hosted in France. They guarantee the sovereignty of your data.
In conclusion
As we have seen previously, the use of a Web Application Firewall (WAF) is proving to be an essential element of web security. UBIKA offers technological solutions that adapt to your needs (web application, API, website) and deployment scope (on-premise, virtualised firewall, deployable on AWS and Azure).
We offer you the white paper “Key Criteria in Choosing a Web Application Firewall” which examines the main elements to consider when selecting a powerful WAAP.